Microsoft gave its high-end Surface a leap forward on Tuesday with the unveiling of the Surface Pro 4 and the surprise launch of the Surface Book, the company’s first laptop.

Microsoft’s love affair with hardware just got more intense. If there were any doubts about the software juggernaut staying in the devices game, they were erased on Tuesday with one of the biggest and broadest hardware announcements in the company’s history.
Microsoft showed off a fleet of new and freshly updated Windows 10-powered devices in New York. The stars of the show were the Surface Pro 4 and the new Surface Book laptop, which were a potent answers to Apple’s recently unveiled iPad Pro and Google’s newly announed Pixel C.
According to Microsoft Devices lead engineer Panos Panay there are nearly 110 million devices running Windows 10. Most of the products Microsoft unveiled at Tuesday’s press event were intended to show how important mobile hardware and software integration with Windows 10 is to the company.
The event’s biggest surprise, the Surface Book, and the new Surface Pro 4 are powerful machines, and both aim to connect with both enterprise users and creative professionals. They succeed big time in the specs department. In terms of usability and adoption, we’ll know more after both are released on October 26.
The Surface Book is Microsoft’s first laptop, and it’s a fiery, ambitious device. The specs are decked, particularly given that the price is comparable to a Macbook Pro. The Surface Book starts at $1499, and comes with a full Intel Core i5 or i7 processor, 1TB of storage, 16GB RAM, and a GPU designed for gaming and multimedia editing by the Xbox team. Additionally, the 13.5-inch screen (3000 x 2000 resolution) can detach to become a stand-alone tablet.
The Surface Pro 4 tablet runs Windows 10 and, like its predecessors, can serve as a full-fledged laptop replacement. The Surface Pro 4 is, as expected, somewhat thinner and 30 percent faster than the previous model. It has 16GB of RAM, and comes with up to a terabyte of storage, and a 12.3-inch screen (2736 x 1824 resolution). Microsoft cloud and productivity apps Cortana, Windows Hello, Microsoft Office, and OneDrive are deeply integrated. The Surface Pro 4 starts at $899.
When the Surface debuted in 2012 running Windows 8, the tablet seemed like an awkward, out-of-place device. Today, the Surface Pro has been owning and innovating in the high-end tablet space. It’s become a favorite of design professionals, IT administrators, and others who want a productivity tablet.
Arguably, the success of the Surface Pro helped pull Apple and Google into the high-end professional tablet market. Google’s comparable new Pixel C is similarly powerful, features a keyboard cover, and is deeply tied to the Google cloud ecosystem. Yet, Google’s device does not feel as durable as the Surface Pro 4, and Office is still often an essential tool for business users looking for a full laptop replacement.
Apple’s iPad Pro is a powerful professional and creative tool. Apple’s high-end tablet is larger and slightly more expensive than the Surface Pro 4. Microsoft is banking that the integration of Windows 10 and universal apps will help the Surface stand on par with the iPad Pro.
Microsoft’s attention to detail with peripheral devices like the Type Pro cover and the Surface Pen stylus may lend them a slight edge in the professional tablet market. The new Surface Pro Type Cover, notable for its “precision glass trackpad” is a significant refinement over the previous generation. The cover still costs 130 dollars, but is lighter, more responsive, and features more space between the keys than the previous version.
Microsoft has worked hard to make the stylus seem useful and cool. The new Surface Pen is intended to feel like writing on paper. The stylus features a tip with 1,024 points of pressure sensitivity, an eraser (yes, an eraser!), year-long battery life, and comes in five colors. When not in use the pen is held snugly to the top of the tablet by magnets. Microsoft took great care to display the tablet tilted in portrait mode like a clipboard, with a pen resting on top. The company emphasized the tablet itself “just fades into the background” when used by office workers, doctors, architects, and musicians.

As with the Surface Pro 4 and Surface Book, the new Lumia 950 and 950 XL phones are powered by Windows 10, with special consideration to mobile productivity. The devices measure at 5.2 and 5.7 inches respectively, and feature an upgraded camera with a dedicated shutter release button.
The most unique and innovative announcement from Microsoft may have been the Display Doc. Intended to maximize workplace flexibility, and uncouple the enterprise user from the constraints of a laptop, the Microsoft Display Doc was initially announced at last spring’s Build conference as the Continuum docking station. The Display Doc is a small, square device that connects to any compatible Windows 10 mobile device like the Lumia 950 using three USB Type-3 ports, a DisplayPort and HDMI. When connected to a monitor using Display Doc, the phone will present a traditional Windows home screen, complete with the familiar Start button and icon tray. Though not as robust as a true desktop PC, the experience resembles desktop Windows and is able to manage productivity tasks like mail and messaging, document creation and sharing, and web browsing.
Windows 10 is at the core of the new Microsoft device environment. The company also announced updates to the Windows 10 universal app ecosystem [LINK], and a launch partnership with Facebook to expand the core Facebook, Messenger, and Instagram applications.
CEO Satya Nadella closed the event by stressing the importance of Windows 10 as a unified platform. Every device Microsoft released on Tuesday is a step towards fulfilling that vision. As impressive as the devices were, the biggest thing standing in their way perhaps is the stability of Windows 10
Have questions?
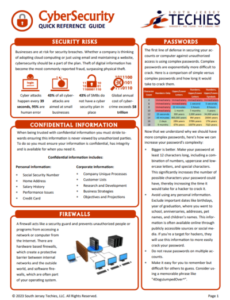
Get help from IT Experts/Microsofts Cloud Solutions Partner
Call us at: 856-745-9990 or visit: https://southjerseytechies.net/
South Jersey Techies, LLC is a full Managed Web and Technology Services Company providing IT Services, Website Design Services, Server Support, Network Consulting, Internet Phones, Cloud Solutions Provider and much more. Contact for More Information.
To read this article in its entirety click here.