Google Chrome, Microsoft Edge, Mozilla Firefox and Apple’s Safari browser have all been impacted by a single zero-day vulnerability. The flaw, tracked as CVE-2023-4863, is caused by a heap buffer overflow in the WebP code library. Once exploited it can lead to system crashes and arbitrary code execution, where hackers can gain control over an infected device.
Where Does it Originate?
CVE-2023-4863 was first identified by researchers at The Citizen Lab, a research arm of the University of Toronto. The institution subsequently informed Google and Apple of the vulnerability’s existence. Both companies have now released patches. They were joined by Mozilla, which released its own advisory on CVE-2023-4863 yesterday and updates for several versions of its Firefox browser and Thunderbird email client, and Microsoft.
Vulnerability Originates In Webp Reader. Users of the affected browsers should update to the most up-to-date version in order to ensure the zero-day vulnerability is patched on their machines. The problem isn’t with the browsers — the vulnerability originates in the WebP Codec. Many applications use the WebP codec and libwebp library to render WebP images.
In more detail, a heap buffer overflow in WebP allowed attackers to perform an out-of-bounds memory write. A heap buffer overflow allows attackers to insert malicious code by “overflowing” the amount of data in a program. Since this particular heap buffer overflow targets the codec (essentially a translator that lets a computer render WebP images), the attacker could create an image in which malicious code is embedded. From there, they could steal data or infect the computer with malware. The vulnerability was first detected by the Apple Security Engineering and Architecture team and The Citizen Lab at The University of Toronto on September 6.
How Dangerous Is This Flaw?
Since many browsers, including Microsoft Edge, Brave, Opera, and Vivaldi are built on the Chromium platform, the same platform that Chrome is based on, this could affect their users as well. The same risk is also applicable for Firefox browser clones.
Such a widespread exploit in ubiquitously used software is dangerous, widening the attack surface for most organizations.
Patching will mitigate the risk, but users must act quickly as hackers will already be at work. Attackers will be working over the coming days and weeks to make the exploit more reliable meaning remote code execution will be more likely. Modern web browsers are exceptionally good at pushing out security updates rapidly and applying them as quickly as practicable, so users will shortly be protected.
The biggest risk is to organizations which don’t allow automatic updates and push out updates at their own release schedule.
What Steps Should You Take?
Google, Mozilla, Brave, Microsoft and Tor have released security patches for this vulnerability. Individuals running those apps should update to the latest version. In the case of other applications, this is an ongoing vulnerability for which patches may not exist; NIST noted that the vulnerability has not yet received full analysis.
If you are already a Managed Services client, please follow the steps below to check for updates
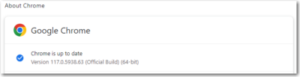
Google Chrome – Click the 3 dots in the top right corner for the menu and choose Help->About Google Chrome. Chrome will check and install updates automatically from this screen.
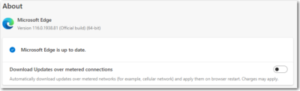
Microsoft Edge – Click the 3 dots in the top right corner for the menu and choose Help and feedback->About Microsoft Edge. Edge will check and install updates automatically from this screen.
Mozilla Firefox – Click the 3 lines in the top right corner for the menu and choose Help->About Firefox. Firefox will check and install updates automatically from this screen.
If you have any questions, please email us at support@sjtechies.com or call us at (856) 745-9990