The must-read IT business eNewsletter

“There is no such thing as perfect security,” says Jim Waldron, Senior Architect for Platform Security at HP. If you can access a website or server, consider it vulnerable to security breaches. That’s why so many businesses account for fraud in their business models—they expect to lose a certain amount each year to security leaks, lost IP, and more.
While you can never be 100% secure from hackers while connected to the internet, there are steps you can take to help protect your personal and professional data. All you need to do is activate features that are increasingly common (or easy to manage) on modern business-class PCs: Multi-factor authentication, client-based user authentication, and password best practices.
Multi-factor authentication
Multi-factor authentication is a simple but effective security system that involves the use of at least two factors (or methods) of authentication. It groups different factors together so that even if one is compromised, the data remains protected. Under this system, factors are divided into three domains:
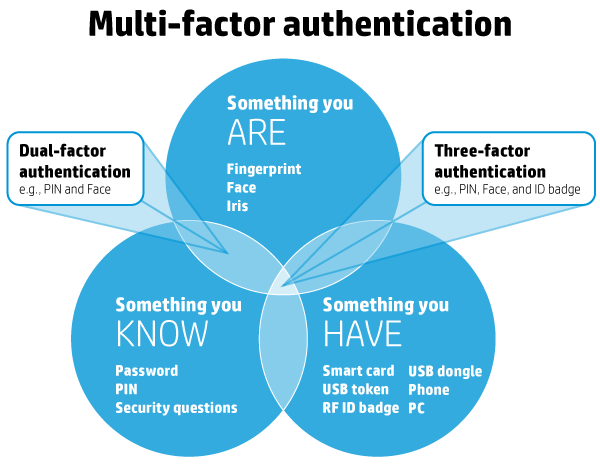
- Something you know: Password, PIN, etc.
- Something you have: ATM card, smartcard, etc.
- Something you are: Fingerprint, iris, etc.
For multi-factor authentication to be successful, you want to pull from at least two different domains, with a maximum of three domains. A common example of multi-factor authentication is when you withdraw cash from an ATM. To do so, you insert your ATM card (something you have) and enter your PIN (something you know). Without both factors you can’t access your account—and neither should anyone else.
Businesses are taking notice too, and multi-factor authentication’s popularity is rising. In 2014, 37% of enterprise organizations surveyed used multi-factor authentication for the majority of their employees, and that number is expected to grow to 56% by 2016.
What you can do now
If you have a business-grade PC, chances are your PC already includes the technologies you need to start using multi-factor authentication. In fact, HP offers multi-factor authentication on all of its business PCs. Consult your manual or HP Support, and identify the factors your PC supports in addition to traditional passwords, such as fingerprint or smartcard readers. Just make sure to choose factors from separate domains.
Client-based user authentication
Every time you log into a system, your identity needs to be authenticated by that system. This process occurs one of two ways: server-side authentication or client-based authentication. With server-side authentication your unencrypted information—such as your password or fingerprint—is sent to a server where it is compared against that server’s records. With client-based authentication, the authentication process—e.g., “Does this fingerprint match the one in our records?”—is performed on the client device, such as your work PC.
While client-based authentication is not as common as its counterpart, it is far more secure. In fact, “In almost all authentication scenarios it is preferable to perform the direct authentication on the client and then communicate an ‘Identity Assurance’ to the relying party,” says Waldron.
Everyone wins when it comes to client-based authentication. The client no longer has to send unencrypted, private information over the internet or store that information on another party’s server, while the relying party no longer has to store sensitive client information on their server—reducing the amount of information that can be stolen if and when a hack occurs.
What you can do now
One of the easiest ways to use client-based authentication is with a hardened fingerprint sensor. The sensor authenticates your fingerprint directly in the hardware, rather than sending it to a server or hard drive, and returns a key that can be used to decrypt password vaults.
Password best practices
As we’ve mentioned before, passwords aren’t perfect. While implementing and using the above features might not seem practical for some of us, everyone can benefit from following basic password best practices. They are quick to implement, and can save you a lot of hassle down the line.
To make the most of your password security, your passwords should be:
- Long—at least 16 characters. Use a password manager to store unique passwords and fill out log-in forms so that you don’t have to memorize them.
- Complex—containing symbols, numbers, uppercase letters, lowercase letters, and spaces (if possible)
- Unique—only use a password once, don’t recycle or repeat across accounts
- Short-lived—the National Cyber Security Alliance suggests changing your password every 60 days
- Difficult to guess—avoid common words found in a dictionary, all or part of your name, repeated letters, or combos that align to your keyboard layout, such as “QWERTY” or “123456”
If you are uncertain whether your password is secure enough or if it meets enough of the criteria above, there are several reliable services that will check your password strength for you. Microsoft’s Safety & Security Center offers a free password checker you can access through your browser, while Mac users can access Apple’s Password Assistant through the Keychain Access utility.
What you can do now
The first thing you can do—right this second—is revise your most important passwords to align with password best practices. That includes your work accounts, personal email, bank accounts, and any other services that contain sensitive data. If you need help remembering your new passwords, consider using a password manager such as HP Password Manager. That way you only have to authenticate once to gain access to all your systems. You can also adopt a system to make your passwords easier to remember. Using acronyms, for example, you can turn the phrase “I was born in 1986 and my parents still live on Lake Street!” into “Iwbi1986ampsloLS!”—creating a strong password that’s easy to remember.
Passwords are changing, and while they will never be perfect, they can still provide an effective first layer of defense against hackers and ne’er do wells. The above features and techniques are increasingly common on modern business PCs, making it easier than ever to protect your private data. All you have to do is use them.
Have questions?
Get help from IT Experts/Microsofts Cloud Solutions Partner
Call us at: 856-745-9990 or visit: https://southjerseytechies.net/
South Jersey Techies, LLC is a full Managed Web and Technology Services Company providing IT Services, Website Design Services, Server Support, Network Consulting, Internet Phones, Cloud Solutions Provider and much more. Contact for More Information.
To read this article in its entirety click here.