From today, Windows users will be able to reserve their upgrade to the new operating system, which has seen its icons revamped by Microsoft.
Microsoft’s next operating system will be available for PCs and tablets from 29th July – with existing Windows users able to reserve their upgrade from today.
Windows 10 will be available both on new PCs and as a free upgrade for those running Windows 7 and 8.1. Owners of these operating systems will see a Windows icon in their taskbar that will allow them to “reserve” their upgrade. The 3GB file can be downloaded from 29th July.
The free upgrade will be available until July next year and those choosing to switch to Windows 10 can cancel their reservations at “at any time”, according to Microsoft.
While Windows 7 Enterprise, Windows 8/8.1 Enterprise and Windows RT/RT 8.1 releases can’t be upgraded in this way, Microsoft has said that “Active Software Assurance customers in volume licensing” will be able to “upgrade to Windows 10 enterprise offerings outside of this offer”. Microsoft are yet to clarify when users of Enterprise versions of Windows will be able to move to Windows 10 Enterprise.
Microsoft is betting Windows 10 will win over users with its ability to run on a variety of platforms, allowing users to use the same cloud services and software as they swap between fixed and mobile computers.
“We designed Windows 10 to run our broadest device family ever, including Windows PCs, Windows tablets, Windows phones, Windows for the Internet of Things, Microsoft Surface Hub, Xbox One and Microsoft HoloLens-all working together to empower you to do great things,” said Terry Myerson, VP of Microsoft’s operating systems group in a blog post.
Features such as Continuum mode will detect when mobile Windows 10 devices are docked with a mouse, keyboard and monitor and reorient the UI to suit – for example switching from tap-friendly tiles to smaller icons suited to a mouse pointer – whileUniversal Apps will tailor their interface to the device they are being used on.
Myerson is keen to stress that “Windows 10 brings back the Start menu” familiar to Windows 7 users, following the backlash against Windows 8’s fullscreen Start menu.
Microsoft is also hoping users will take to Cortana, the built-in virtual assistant that users can talk to in order to set appointments, search for information and answer rudimentary queries, and which should become more capable as it learns more about you.
Windows 10 will include the free anti-malware software Windows Defender, which will have free updates for the lifetime of the OS, as well as its new faster and more capable Edge web browser.
While the operating system will launch on PCs and tablets in July, it is expected tolaunch on phones, small tablets, Xbox, and Hololens at unspecified later dates.
Microsoft said it had refined the OS using feedback from more than four million Windows Insiders testing early builds of the OS.
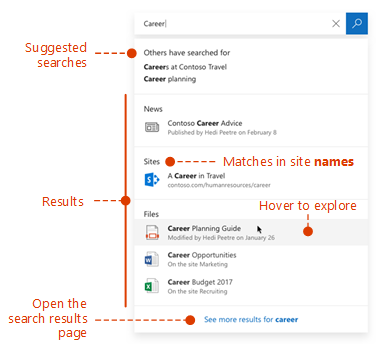
The firm revealed a new, or at least slightly tweaked, look for Windows 10, in its latest Build 10130, which has just been made available via the Windows Insider programme.
The update overhauls the rather plain icons present in earlier builds and replaces them with what Microsoft describes as “more modern and lightweight” alternatives. The revamp means that app icons will also be more consistent between desktop and mobile in apps such as Word and Excel.
While the new icons may not look vastly different, Microsoft said extensive work had gone into the redesign.
“Between the legacy aero-style icons and new app icons, several thousand icons were designed and redesigned. We explored Swiss graphic design, Dutch product design, and modern architecture (among other design fields and styles) to inform and inspire the design process. The icon evolution will continue as we push more consistency and better functionality,” according to a blog post.
Other improvements in the latest build include the ability to customise the Start menu, a new look for Jump Lists on the Taskbar, new swipe shortcuts for Tablet mode, the addition of a Favorites pane and other features to the Edge browser, Taskbar settings for Virtual Desktops, a Cortana keyboard shortcut, Print to PDF feature and fullscreen playback for the Movies & TV app.
Have questions?
Our small business team is here to help.
Call us at: 856-745-9990
South Jersey Techies, LLC is a full Managed Web and Technology Services Company providing IT Services, Website Design Services, Server Support, Network Consulting, Internet Phones, Cloud Solutions Provider and much more. Contact for More Information.