Takeaway: It’s official. Verizon is getting the iPhone. There are five big questions that we’ve been hearing in relation to the iPhone 4 launch on Verizon. Here are the answers.
It’s official. AT&T’s deal as the exclusive US carrier for the iPhone has ended (apparently the 4-year deal concluded at the end of 2010), and Verizon is the first new US telecom to add the iPhone to its roster. The long-anticipated move was announced at a Verizon press event at New York’s Lincoln Center on Tuesday in the midst of a circus atmosphere that included the tech press, all of the national news networks, and even The Daily Show.
The iPhone 4 will arrive on Verizon on February 10. Current Verizon customers will be able to pre-order online starting February 3. The price of the iPhone will remain the same: $199 for 16GB and $299 for 32GB, with a two-year Verizon contract. As for the price of Verizon data plans for the iPhone, Verizon coyly stated, “Customers will also be required to activate a data package. Pricing will be announced at a later date.”
It’s odd that the iPhone wouldn’t simply use the existing Verizon 3G data plans. This seems to indicate a couple possible scenarios. Either: 1.) Verizon is going to have a special data plan just for the iPhone (it has been rumored that Verizon would offer a truly unlimited data plan for iPhone), or 2.) Verizon is about to change the price of all of its 3G data plans in conjunction with the iPhone launch.
Beyond the basic details, here are answers to five big questions that we’ve been hearing from our audience in relation to the iPhone finally landing on Verizon:
1. Will it be CDMA or LTE?
Unfortunately, the iPhone 4 will only run on Verizon’s 3G CDMA network and not on its newly-launched 4G LTE network. This was the biggest disappointment of the Verizon iPhone announcement, especially since upcoming Android devices like the HTC Thunderbolt and Motorola Droid Bionic will be running on the LTE superhighway in a few months. At CES last week I tested the HTC Thunderbolt on the Verizon LTE network and was blown away by the desktop-like speeds for loading Web pages. At today’s press event Apple said that including LTE in the iPhone 4 would have involved “design compromises” (probably in size and battery life) and would have taken longer before it was ready to launch. However, both Apple and Verizon stated that this is just the beginning of their partnership (Translation: Expect an LTE-capable iPhone in the future).2. Will it have mobile hotspot capability?
The biggest surprise of the Verizon iPhone announcement — and arguably the biggest news of the press conference since everything else was pretty much as expected — was that the Verizon version of the iPhone will offer the capability of turning itself into a mobile hotspot that can share its 3G Internet connection over Wi-Fi with up to five devices. Again, no information was provided on whether Verizon will charge extra for mobile hotspot capability. Verizon has wide variations in its treatment of tethering and mobile hotspot charges. It has charged Android users an additional fee for it, but threw it in for free to Palm Pre Plus users. What they do with the iPhone will probably depend on how aggressively the company wants to try to poach current AT&T iPhone customers.3. Does new Verizon model fix iPhone 4’s antenna?
As you’ve probably heard, when the iPhone 4 first launched last June there were a bunch of customers who experienced antenna problems when holding the iPhone in a way that covered a sensitive portion of the antenna in the lower left-hand corner of the phone. The problem was drastically overblown by the tech press and drastically understated by Apple. In the end, Apple said the problem was significantly reduced if you use an iPhone case and offered free cases to buyers. A number of people have asked if Apple has fixed the problem in this new iteration of the iPhone 4 for Verizon. Naturally, Apple hasn’t said that it has changed anything with the iPhone antenna, but a closer look at the Verizon iPhone shows that it does indeed have a different antenna design and early reports indicate that the Verizon iPhone is not exhibiting the antenna problems.4. Can you transfer an existing iPhone to Verizon?
The AT&T version of both the iPhone 3GS (which just got a price drop to $50) and iPhone 4 are built on what’s called GSM radio technology (used by both AT&T and T-Mobile in the US). Meanwhile, Verizon and Sprint use a completely different technology called CDMA. The two standards are incompatible. They use different radios and operate on different wireless frequencies. So, no, you cannot take your existing AT&T iPhone and walk into a Verizon store and simply switch networks. Even if you own an iPhone 4 you will have to purchase a completely new iPhone 4 with CDMA chips in order for it to work on Verizon.5. Will iPhone kill Verizon’s network like it did to AT&T?
Another question that we heard a lot leading up to the expected announcement of the Verizon iPhone today was whether the influx of millions of new iPhone users would bring the Verizon network to its knees the same way it has crushed the AT&T network in areas such as New York, San Francisco, and Los Angeles and at big events like CES and SXSW. I think the answer is “no,” for several reasons. First of all, Verizon is a lot more serious than any of the other US wireless carriers when it comes to network integrity. They aggressively test and audit their own network, so I’ll think they’ll be ready. Second, they just beefed up all of their cell sites to handle additional bandwidth and network load for the launch of their 4G LTE network in 38 cities and they are in the process of upgrading the rest of the US to LTE over the next 24-36 months. Third, while there will be plenty of existing Verizon customers who jump on board with the iPhone and some die-hards who jump from AT&T to Verizon, the vast majority of iPhone customers will remain on AT&T because they are under contract and leaving would be prohibitively expensive.To view the original article in it’s entirety, Click Here






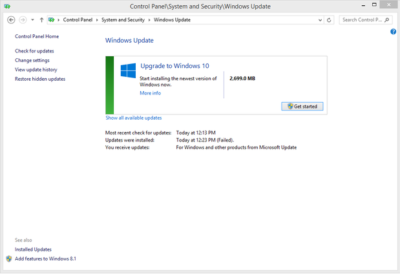
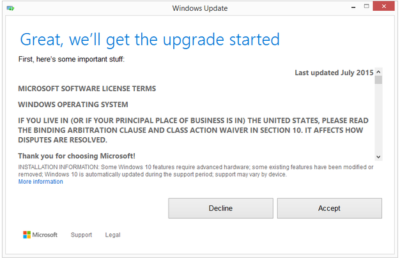






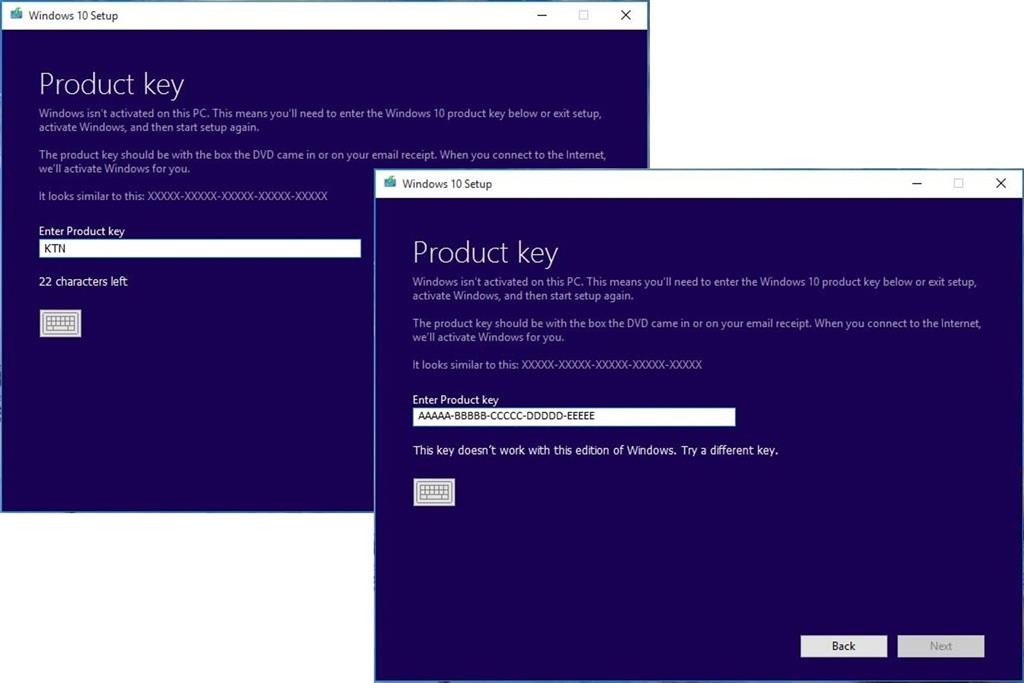
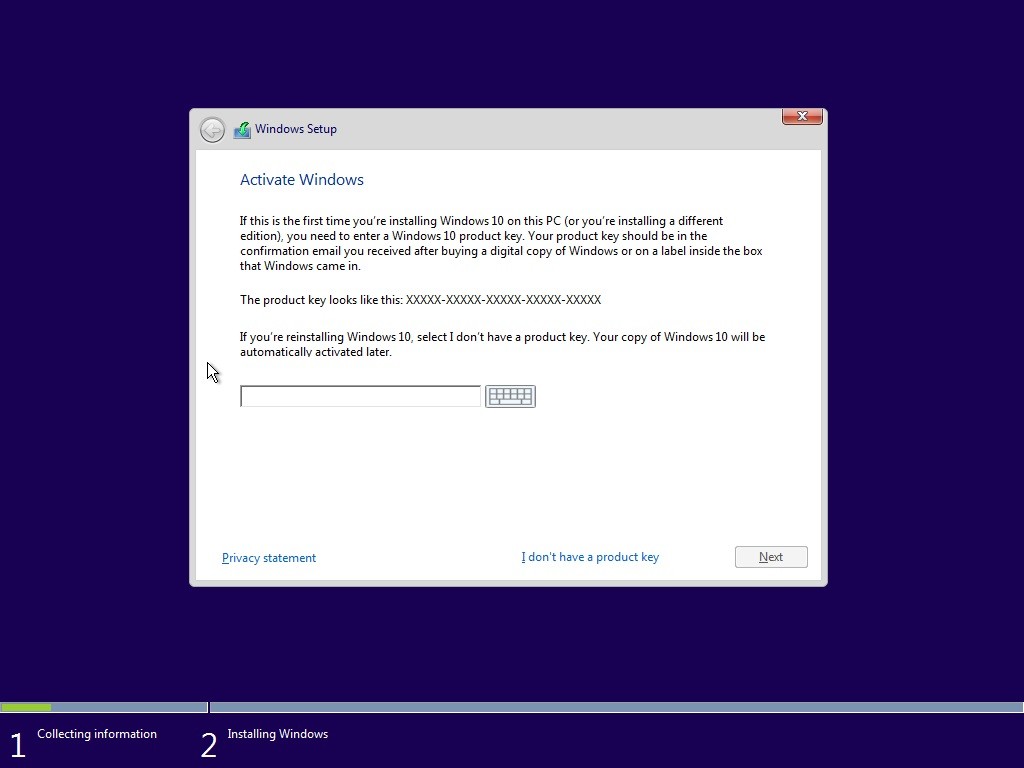
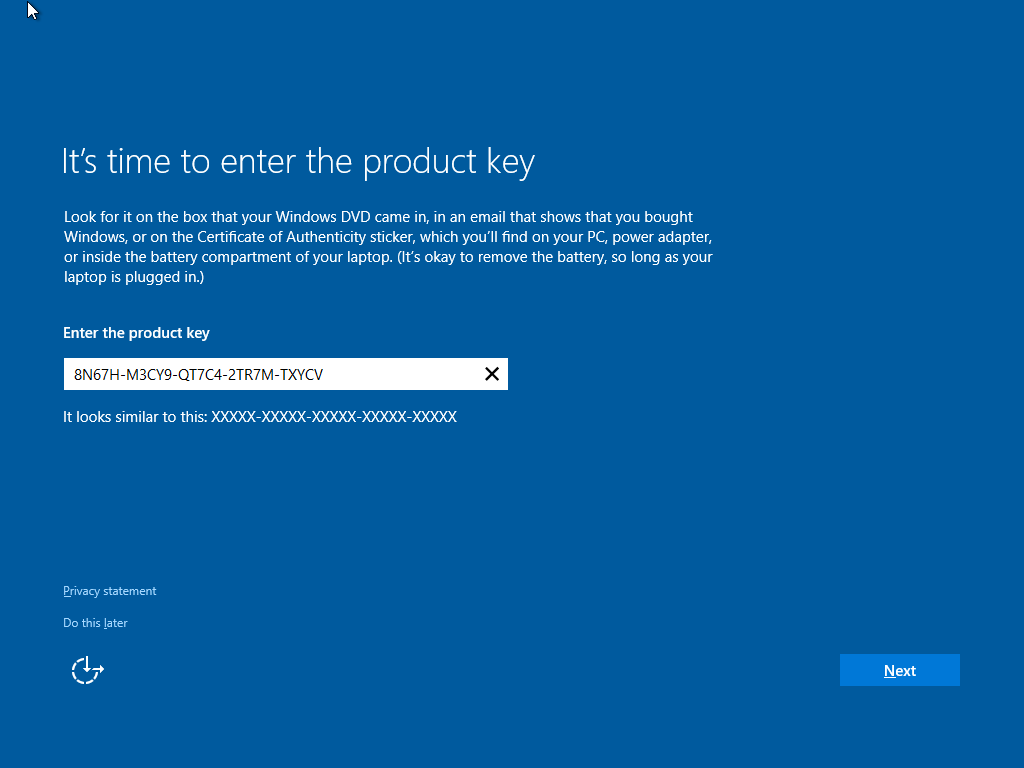 Suppose you decide to reinstall Windows 7 or Windows 8?You can reinstall or restore a system image of your previous version of Windows and continue using it, this will not affect the validity of the license.If you continue to experience problems entering your product key:
Suppose you decide to reinstall Windows 7 or Windows 8?You can reinstall or restore a system image of your previous version of Windows and continue using it, this will not affect the validity of the license.If you continue to experience problems entering your product key: