Microsoft has changed the look of the Start menu in Windows 10.
The revamped Start menu is due to be added to Windows 10 this summer, as part of a major update coined the ‘Windows 10 Anniversary Edition’.
Microsoft revealed the updated appearance in an early build of the OS, which it released to testers in the Windows 10 Insider program on Friday.
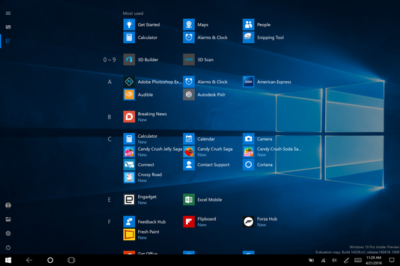
The new look Start menu makes the ‘All Apps’ list visible by default on the left-hand side. In another new addition, a selection of the user’s ‘Most-used’ apps are shown at the top of this permanently visible ‘All Apps’ list. Microsoft says the change should reduce the clicking and scrolling needed to access apps.
The Power, Settings and File Explorer icons are also always visible in the left rail of the Start menu and the ‘Recently added’ section will display three entries, instead of one. Any folders that users have added to the Start menu are now immediately accessible without having to click the hamburger icon.
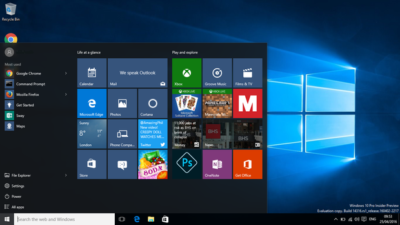
The old look start menu
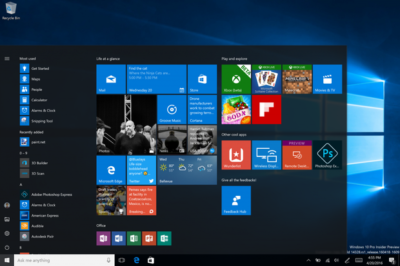
The new look start menu
The look of the Start menu in tablet mode has also been overhauled, turning the ‘All Apps’ list into a fullscreen menu, reminiscent of the Windows 8.1 Start screen. Gabe Aul, VP for Microsoft’s engineering systems team, says the switch to fullscreen was a ‘top request from Windows Insiders’, adding that ‘the grid-like implementation of the full-screen ‘All Apps’ list aims to provide efficiency while taking advantage of the additional real estate on the Start screen on a tablet’.
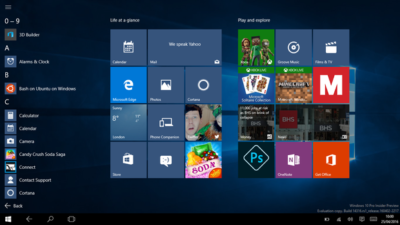
The old look ‘All Apps’ list in tablet mode.
The new look ‘All Apps’ list in tablet mode.
The final Start menu change is designed to make it easier to toggle between pinned tiles and the ‘All Apps’ list, by providing the option to do so in the menu’s left rail.
More helpful Cortana and other changes
The latest Windows Insider build, 14328, also includes a raft of features that will be available to all users following the Anniversary Update.
These new components include Windows Ink, which allows users to more easily write notes on touchscreen PCs and tablets using a digital pen. The addition of Windows Ink to Windows 10 allows users to write on digital sticky notes, draw on digital whiteboards and annotate content in a variety of apps, including Maps, Microsoft Edge, and Office. Microsoft wants support for drawing and writing using a digital pen to be present in many Windows 10 apps and says that adding support for Windows Ink only requires developers to write two lines of code.
Windows 10’s digital assistant Cortana has also been tweaked. Users will no longer have to log into Windows to use Cortana and instead will be able to use voice commands to get Cortana to make notes, play music or set a reminder from the lock screen.
Cortana can now also be used to set photo reminders, for example the user could take a picture of a cheese they want to buy next time they’re in a store, and add reminders based on content from another Windows 10 app, for example telling a user to read an article they flagged as interesting in the Edge browser. Cortana is now also accessible to all users, with Windows 10 no longer requiring users to sign-in before they can ask simple questions of the digital assistant.
Other changes include the ability to search files on OneDrive cloud storage that aren’t synced locally, tweaks to the look of and what is displayed in the Action Center and via notifications, various changes to the Taskbar — including easier access to the calendar and the removal of the File Explorer icon, as well as updates to the Settings app and lock screen.
As this is an early build of Windows 10, some of these features may change before reaching the general public, based on feedback from testers in the Windows Insider program.
Have questions?
Get answers from Microsofts Cloud Solutions Partner!
Call us at: 856-745-9990 or visit: https://southjerseytechies.net/
South Jersey Techies, LL C is a full Managed Web and Technology Services Company providing IT Services, Website Design Services, Server Support, Network Consulting, Internet Phones, Cloud Solutions Provider and much more. Contact for More Information.