Check out a recently developed and designed website by South Jersey Techies Website Team for Wayne R. Miller & Company in Moorestown, NJ.

BigBeagle.com Category
Check out a recently developed and designed website by South Jersey Techies Website Team for Wayne R. Miller & Company in Moorestown, NJ.


Business leaders must prepare for disasters made by man or Mother Nature with extensive, practiced recovery plans to avoid system shutdowns.
A Delta ground stop was lifted Monday morning following a 2:30 a.m. ET power outage in Atlanta that delayed and cancelled flights worldwide. Businesses should view this as a cautionary tale, highlighting the importance of quality data center power and disaster control systems.
Delta cancelled approximately 300 flights due to the outage. As of 10:30 a.m. ET, it operated 800 of its nearly 6,000 scheduled flights. However, Delta customers heading to the airport on Monday should still expect delays and cancellations, according to a press release. As inquiries are high and wait times are long, there may also be some lag time in the display of accurate flight status from the airline, it warned.
Last month, Southwest Airlines cancelled 1,150 flights after a system outage. Though the system came back online within the day, hundreds of flights were backlogged.
Based on recent research, it’s fair to say that what happened to Delta and Southwest could happen to a number of businesses. Some 57% of small and mid-sized businesses have no recovery plan in the event of a network outage, data loss, or other IT disaster, according to a Symantec study.
“Planning and executing disaster recovery exercises is something that should be done on a regular basis to find out these issues before they may be impactful,” said Mark Jaggers, a Gartner data center recovery and continuity analyst. “The issue, which was also the case with Southwest Airlines, is not planning for partial failure scenarios that are harder to get to the root cause of and work around.”
To avoid shutdowns like Delta’s, company data centers should have redundant power and networking, preferably from a grid and provider, respectively, that are completely independent from the primary ones, Jaggers said.
“Data centers are a huge piece of a disaster recovery plan,” said mission-critical facility management professional Christopher Wade. “To have a reliable infrastructure, you have to minimize single points of failure.” Business leaders should also ask about the experience levels of data center staff, as many of these companies are currently understaffed, Wade added.
Usually, large companies have a primary data center in one location and an alternate in another that is far enough away so the two do not experience the same disaster at the same time, said Roberta Witty, risk and security management analyst at Gartner.
“In today’s world, the business expectation is that you’re up and running quickly after a disaster,” Witty said. “The ‘always on’ driver is changing the way organizations deliver IT in general, and so they are building out their data centers to be more resilient.”
About 60% of organizations are moving to a recovery time objective of four hours or less, Witty said. Doing so successfully involves extensive planning. First, determine what business operations are mission critical. Then, consider factors that impact recovery time requirements, such as revenue loss, safety, and brand reputation, and build your recovery infrastructure accordingly. As more companies outsource data operations, a key consideration should be the third party’s ability to meet your recovery requirements, she added.
Crisis management practices, such as the procedures Delta used to notify management and deal with customer fallout, usually get exercised every quarter. “The more you practice your crisis management procedure and communicating with your workforce, customers, suppliers, and partners, the better off you are,” Witty said. “A plan that hasn’t been exercised is not a workable plan.”
Disaster recovery can’t be something a company reviews once a year, Witty said, but rather an ongoing part of every new project.
“Your recovery environment has to stay in sync with production, which is where a lot of organizations fail,” Witty said. “Build disaster recovery into a project lifestyle—whether it’s a new product or a change in management, you have to go back and revisit your recovery plans.”
Get answers from Microsofts Cloud Solutions Partner!
Call us at: 856-745-9990 or visit: https://southjerseytechies.net/
South Jersey Techies, LL C is a full Managed Web and Technology Services Company providing IT Services, Website Design Services, Server Support, Network Consulting, Internet Phones, Cloud Solutions Provider and much more. Contact for More Information.
To read this article in its entirety click here.

The hackers used “ransomware” to lock the hospital out of its own medical records.
Not all kidnappers grab your loved ones.
A growing online threat – ransomware – essentially abducts your computer system, putting data and services off-limits to users and demanding a payment to restore access.
“We are seeing more cases of this – sometimes almost on a daily basis,” said New Jersey State Police Capt. Steve Jones. “And we’re not seeing all of it, because people may be too embarrassed or don’t believe it can be helped.”
Ransomware viruses are a plague. Once infected — installed to your computer by a website you’ve visited, a rogue email attachment or link, or instant message — your computer will lock up. With names like CryptoWall, these types of viruses may create a popup window or Web page warning you that you’ve broken some law and have to pay a fine, anywhere from hundreds to thousands of dollars, according to the FBI.
These scams threaten to encrypt your files forever or destroy them unless a ransom is paid, according to the FBI.
Once paid, your computer is unlocked or a code is sent to unlock the machine, authorities said.
Between April 2014 and June 2015, the FBI received 992 CryptoWall-related complaints with victims reporting a loss of more than $18 million.
The state’s top cybersecurity unit recently launched an online effort to help people guard against ransomware.
“For many organizations, preventing ransomware entirely is nearly impossible,” says the New Jersey Cybersecurity and Communications Integration Cell (NJCCIC), which introduced a Ransomware Threat Profile page at its website in February.
But it notes individuals and companies can take measures to prevent infections and to limit their impact.
Although ransomware can lock up laptops and desktop computers, the risk is particularly great for data-dependent organizations like hospitals and accounting firms, said Jones, the State Police spokesman.
So far, at least three hospitals have been hit nationwide – in California, Kentucky and the Washington, D.C., area. South Jersey hospitals are well aware of the menace.
“It’s a big concern. It’s something that has really spiked,” said Tom Handlon, chief information security officer for Kennedy Health, which operates three acute-care hospitals in South Jersey.
Handlon gave no details, but said Kennedy seeks to protect itself through protective measures inside its computer system and by promoting safe conduct by employees.
“We’re monitoring it constantly and updating as we go along,” he said. “We are really educating the staff and our entire organization that we are a target.”
A similar view came from Tom Rubino, spokesman for Cooper University Healthcare System in Camden.
“We have tracked the recent wave of ransomware attacks that have targeted hospitals across the nation,” Rubino said. He said Cooper’s IT security team “is proactively taking measures to prevent ransomware infection of our computer systems.”
“Additionally, as a critical component for preventing all computer viruses, we are increasing our employee education efforts.”
A key precaution is to back up your computer’s contents on a frequent basis, Jones said. “But you’ve got to keep the backup drives disconnected,” he warned. “Otherwise, the ransomware can migrate to the backups.”
The State Police in March 2015 investigated a hacking incident that disabled much of the computer system for the Swedesboro-Woolwich school system. In that case, a hacker demanded more than $125,000 in the form of a digital currency called bitcoins.
The district, which did not pay the ransom, had to wipe clean its email servers and cafeteria lunch-ordering system to rid itself of ransomware. Only a handful of classroom computers were infected.
Hackers exploited a gap in the district’s computer security system and a vendor’s “weak” passport to take over the computer system, Michael Procopio, Educational Information and Resource Center’s director of technology, said at the time. EIRC experts helped the district restore its system.
The district’s hacker was believed to have struck from abroad – a familiar pattern, according to the State Police.
“Many of these messages and attacks are coming through foreign servers,” Jones said. “The countries that house these servers are not often countries that have a real open relationship with law enforcement.”
Tools have been available to help decrypt older versions of ransomware, said Dave Weinstein, New Jersey’s director of cybersecurity.
“At this point, the strain has morphed to the point where there is no releasing your files,” said Al Della Fave, a spokesman for the Ocean County Prosecutor’s office. “The lock these cybercriminals put on your files is foolproof at this point.”
Unless you’ve backed up your computer prior to the infection, Della Fave said, “The only way you would get your files back is to pay.”
“Ransomware is working” for cyberthieves, said Ben Johnson, chief security strategist at Carbon Black Inc., a computer security firm in Waltham, Massachusetts. “People are paying.”
In the last few weeks, cybercriminals have come up with some new twists, he said. For instance, one version encrypts files more quickly after someone opens up a malware-filled Microsoft Word document or some other attachment.
Other versions encrypt the computer at its most basic level so it can’t even power on, or use the computer’s own system administration tools to infect itself, he said.
The best course of action is to make sure you don’t get the virus. “You must be super careful what you click on,” Della Fave said.
Here’s what you should do, according to Johnson and the Ocean County prosecutor’s office:
Get answers from Microsofts Cloud Solutions Partner!
Call us at: 856-745-9990 or visit: https://southjerseytechies.net/
South Jersey Techies, LL C is a full Managed Web and Technology Services Company providing IT Services, Website Design Services, Server Support, Network Consulting, Internet Phones, Cloud Solutions Provider and much more. Contact for More Information.
To read this article in its entirety click here.

There’s plenty of free, effective anti-malware protection available. Just don’t let it push your browser around.
Although malware was once predicted to become extinct, it remains a constant threat. Thankfully, countless tools are available to help protect your PC against such security threats—including the popular (and free) anti-malware products on this list.
AVG AntiVirus Free (Figure A) provides protection for your computer, your browser, and your mail client. Like many other free products, AVG AntiVirus Free tries to sell you a paid license, which includes an enhanced firewall, anti-spam protection, and a few other features.
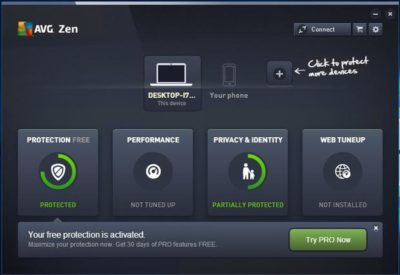
Although AVG AntiVirus Free seems to do a good job protecting systems against viruses, you have to be careful about the options you choose when installing and configuring this product. Otherwise, AVG will attempt to “hijack” your browser by installing AVG Web TuneUp, changing your search page, changing your new tab pages, and changing your home page.
Malwarebytes Anti-Malware Free (Figure B) offers basic protection against malware. There are two main things I like about this app. First, unlike some of the other free anti-malware products, it doesn’t try to change your browser settings or install unwanted toolbars. Second, it has a clean and intuitive interface that doesn’t leave you guessing about what to do.
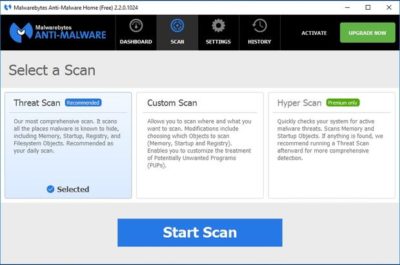
The disadvantage to using Malwarebytes Anti-Malware Free is that unlike the premium version, it does not support real-time protection. You can scan your PC for malware at any time, but you won’t be alerted to infections in real time unless you upgrade to the paid version.
Avast Free Antivirus 2016 (Figure C) is probably the most comprehensive antivirus tool on this list. It offers 12 components, including Rescue Disk, Browser Cleaner, Web Shield, and File Shield. The installer lets you choose which components to install.
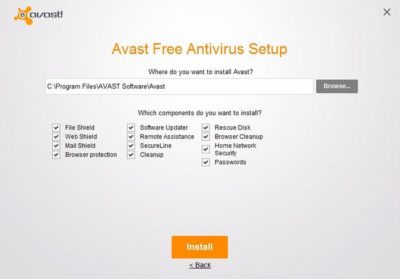
During the hour or so that I used Avast Free Antivirus, it did not attempt to take over my browser or engage in any other obnoxious behavior. The software does, however, prominently display a warning message during the installation process telling you in no uncertain terms that Avast Free Antivirus 2016 collects personal information. At least it gives you a way to opt out of this data collection.
Panda Free Antivirus (Figure D) is another free anti-malware solution that requires a bit of caution during the installation process—otherwise, Panda will install a browser toolbar and change your home page and your default search provider.
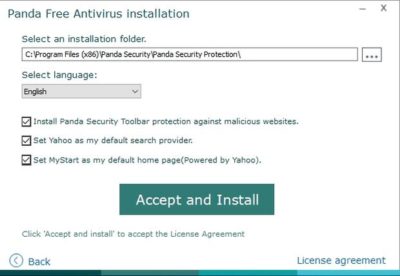
The free version of Panda Antivirus offers real-time protection against malware, but it does try to get you to upgrade to the paid version. That version, which Panda refers to as the Pro Edition, adds a firewall, Wi-Fi protection, and VIP support.
YAC (Figure E) stands for Yet Another Cleaner and—you guessed it—it’s yet another free tool for blocking threats and removing malware from an infected system. It offers a simple, easy-to-follow interface, and it doesn’t try to hijack your browser (which is a personal pet peeve, in case you hadn’t noticed). In fact, the software gives you a way to lock your browser settings so that your preferred home page, default browser, and default search engine can’t be changed without your consent.
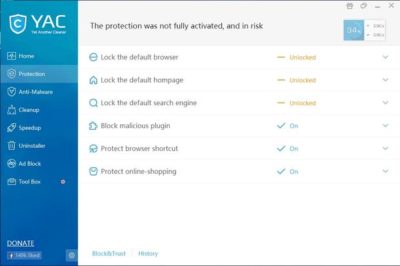
In addition to its basic anti-malware capabilities, YAC includes some nice extras, such as a tool for speeding up your computer, an uninstaller, and an ad blocker. The primary disadvantage to using YAC is that you have to upgrade to the paid version if you want to receive real-time protection. Otherwise, you’ll have to initiate anti-malware scans manually.
Get answers from Microsofts Cloud Solutions Partner!
Call us at: 856-745-9990 or visit: https://southjerseytechies.net/
South Jersey Techies, LL C is a full Managed Web and Technology Services Company providing IT Services, Website Design Services, Server Support, Network Consulting, Internet Phones, Cloud Solutions Provider and much more. Contact for More Information.
To read this article in its entirety click here.
Takeaway: Windows Server 2012 is generating a significant buzz among IT pros. Deb Shinder highlights several notable enhancements and new capabilities.
We’ve had a chance to play around a bit with the release preview of Windows Server 2012. Some have been put off by the interface-formerly-known-as-Metro, but with more emphasis on Server Core and the Minimal Server Interface, the UI is unlikely to be a “make it or break it” issue for most of those who are deciding whether to upgrade. More important are the big changes and new capabilities that make Server 2012 better able to handle your network’s workloads and needs. That’s what has many IT pros excited.
Here are 10 reasons to give serious consideration to upgrading to Windows Server 2012 sooner rather than later.
A Server Core installation provides security and performance advantages, but in the past, you had to make a commitment: If you installed Server Core, you were stuck in the “dark place” with only the command line as your interface. Windows Server 2012 changes all that. Now we have choices.
The truth that Microsoft realized is that the command line is great for some tasks and the graphical interface is preferable for others. Server 2012 makes the graphic user interface a “feature” — one that can be turned on and off at will. You do it through the Remove Roles Or Features option in Server Manager.
Speaking of Server Manager (Figure A), even many of those who dislike the new tile-based interface overall have admitted that the design’s implementation in the new Server Manager is excellent.
One of the nicest things about the new Server Manager is the multi-server capabilities, which makes it easy to deploy roles and features remotely to physical and virtual servers. It’s easy to create a server group — a collection of servers that can be managed together. The remote administration improvements let you provision servers without having to make an RDP connection.
The Server Message Block (SMB) protocol has been significantly improved in Windows Server 2012 and Windows 8. The new version of SMB supports new file server features, such as SMB transparent failover , SMB Scale Out, SMB Multichannel, SMB Direct, SMB encryption, VSS for SMB file sharing, SMB directory leasing, and SMB PowerShell. That’s a lot of bang for the buck. It works beautifully with Hyper-V, so that VHD files and virtual machine configuration files can be hosted on SMB 3.0 shares. A SQL system database can be stored on an SMB share, as well, with improvements to performance. For more details about what’s new in SMB 3.0, see this blog post.
Even though some say Microsoft has shifted the focus away from security in recent years, it would be more accurate to say it has shifted the focus from separate security products to a more “baked in” approach of integrating security into every part of the operating system.
Dynamic Access Control is one such example, helping IT pros create more centralized security models for access to network resources by tagging sensitive data both manually and automatically, based on factors such as the file content or the creator. Then claims based access controls can be applied. Read more about DAC in my “First Look” article over on Windowsecurity.com.
Storage is a hot — and complex — topic in the IT world these days. Despite the idea that we’re all going to be storing everything in the public cloud one day, that day is a long way off (and for many organizations concerned about security and reliability, it may never happen). There are myriad solutions for storing data on your network in a way that provides better utilization of storage resources, centralized management, and better scalability, along with security and reliability. Storage area networks (SANs) and network attached storage (NAS) do that, but they can be expensive and difficult to set up.
Storage Spaces is a new feature in Server 2012 that lets you use inexpensive hard drives to create a storage pool, which can then be divided into spaces that are used like physical disks. They can include hot standby drives and use redundancy methods such as 2- or 3-way mirroring or parity. You can add new disks any time, and a space can be larger than the physical capacity of the pool. When you add new drives, the space automatically uses the extra capacity. Read more about Storage Spaces in this MSDN blog post.
Virtualization is the name of the game in the server world these days, and Hyper-V is Microsoft’s answer to VMware. Although the latter had a big head start, Microsoft’s virtualization platform has been working hard at catching up, and many IT pros now believe it has surpassed its rival in many key areas. With each iteration, the Windows hypervisor gets a little better, and Hyper-V in Windows Server 2012 brings a number of new features to the table. One of the most interesting is Hyper-V Replica.
This is a replication mechanism that will be a disaster recovery godsend to SMBs that may not be able to deploy complex and costly replication solutions. It logs changes to the disks in a VM and uses compression to save on bandwidth, replicating from a primary server to a replica server. You can store multiple snapshots of a VM on the replica server and then select the one you want to use. It works with both standalone hosts and clusters in any combination (standalone to standalone, cluster to cluster, standalone to cluster or cluster to standalone). To find out more about Hyper-V replica, see this TechNet article.
Windows Terminal Services has come a long way, baby, since I first met it in Windows NT TS Edition. Renamed Remote Desktop Services, it has expanded to encompass much more than the ability to RDP into the desktop of a remote machine. Microsoft offered a centralized Virtual Desktop Infrastructure (VDI) solution in Windows Server 2008 R2, but it was still a little rough around the edges. Significant improvements have been made in Server 2012.
You no longer need a dedicated GPU graphics card in the server to use RemoteFX, which vastly improves the quality of graphics over RDP. Instead, you can use a virtualized GPU on standard server hardware. USB over RDP is much better, and the Fair Share feature can manage how CPU, memory, disk space, and bandwidth are allocated among users to thwart bandwidth hogs. Read more about Server 2012 VDI and RDP improvements here.
DirectAccess was designed to be Microsoft’s “VPN replacement,” a way to create a secure connection from client to corporate network without the performance drain and with a more transparent user experience than a traditional VPN. Not only do users not have to deal with making the VPN work, but administrators get more control over the machines, with the ability to manage them even before users log in. You apply group policy using the same tools you use to manage computers physically located on the corporate network.
So why hasn’t everyone been using DirectAccess with Server 2008 R2 instead of VPNs? One big obstacle was the dependency on IPv6. Plus, it couldn’t be virtualized. Those obstacles are gone now. In Windows Server 2012, DirectAccess works with IPv4 without having to fool with conversion technologies, and the server running DirectAccess at the network edge can now be a Hyper-V virtual machine. The Server 2012 version of DA is also easier to configure, thanks to the new wizard.
Despite the many advantages NTFS offers over early FAT file systems, it’s been around since 1993, and Windows aficionados have been longing for a new file system for quite some time. Way back in 2004, we were eagerly looking forward to WinFS, but Vista disappointed us by not including it. Likewise, there was speculation early on that a new file system would be introduced with Windows 7, but it didn’t happen.
Windows Server 2012 brings us our long-awaited new file system, ReFS or the Resilient File System. It supports many of the same features as NTFS, although it leaves behind some others, perhaps most notably file compression, EFS, and disk quotas. In return, ReFS gives us data verification and auto correction, and it’s designed to work with Storage Spaces to create shrinkable/expandable logical storage pools. The new file system is all about maximum scalability, supporting up to 16 exabytes in practice. (This is the theoretical maximum in the NTFS specifications, but in the real world, it’s limited to 16 terabytes.) ReFS supports a theoretical limit of 256 zetabytes (more than 270 billion terabytes). That allows for a lot of scaling.
Anyone who has worked with server licenses might say the very term “simplified licensing” is an oxymoron. But Microsoft really has listened to customers who are confused and frustrated by the complexity involved in finding the right edition and figuring out what it’s really going to cost. Windows Server 2012 is offered in only four editions: Datacenter, Standard, Essentials, and Foundation. The first two are licensed per-processor plus CAL, and the latter two (for small businesses) are licensed per-server with limits on the number of user accounts (15 for Foundation and 25 for Essentials).
To View Full Article Click Here

Office 365 provides the productivity tools required by a modern enterprise workforce. This guide covers key details, including available applications, system requirements, and subscription options.

For just about any enterprise of any size, the productivity of its modern workforce revolves around the basic office suite of email, calendar, word processor, and spreadsheet. But as the enterprise workforce has become more mobile, the basic productivity toolset has had to adapt and change to match new requirements. This is why Microsoft updated Office 365 to be a mobile collaborative platform ready to get work done wherever and whenever it happens.
Microsoft Office 365 is the de facto productivity suite for many enterprises and it is the suite all the other competitors are measured against. So as a leader in information technology for your enterprise, it’s in your best interest to know everything there is to know about Office 365. To help you achieve that goal, TechRepublic compiled the most important details and related resources on Microsoft Office 365 into this “living” guide, which we’ll periodically update as new information becomes available.
What is it? Microsoft Office 365 provides users with the basic productivity applications necessary to get work done in the modern enterprise. It includes applications like Word, Excel, Outlook, PowerPoint, OneNote, and OneDrive, just to name a few.
Why does it matter? As the standard for productivity suites, competing products are generally measured against applications from the Office 365 suite.
Who does it affect? In the modern mobile-centric enterprise, Office 365 provides the tools used to get work done. This makes Office 365 important to just about every working individual.
When is it available? The latest version of Microsoft Office 365 is available right now. The current subscription includes Office 2016 applications.
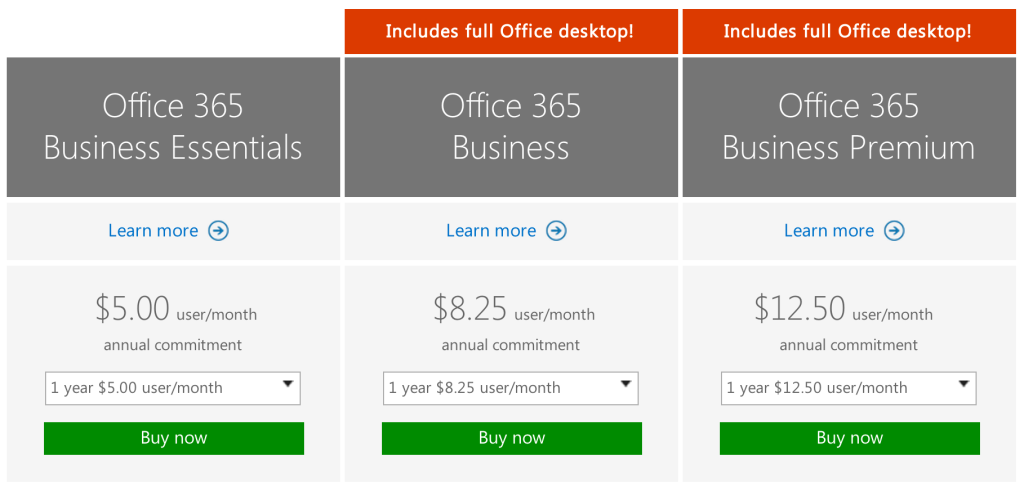
How do you get it? Enterprises can purchase a subscription to Office 365 via the Microsoft website. Subscriptions range from $8/user/month to $35/user/month.
Microsoft Office 365 is a subscription service that provides users with the basic productivity applications necessary to get work done in the modern enterprise. Productivity applications include, but are not limited to, a word processor, a spreadsheet, an email client, a calendar, and a presentation application.

As an example, a Business Premium subscription to Office 365 ($12.50 per person per month) includes these applications:
Word: This app sets the standard for word processors and is available with Office 365 for both Business and Premium. If users in your enterprise need to create documents, this is the tool they will use.
Excel: The spreadsheet has been the workhorse for basic data analysis since its invention back in the previous century. Excel is the current standard-bearer and comes with Office 365 for Business and Premium.
Outlook: Office 365’s solution for managing email and an appointment calendar is called Outlook. The app has been around for many years and its busy interface tends to be either loved or hated by users. It’s available with both the Business and Premium subscriptions.
PowerPoint: Communicating information to a group of individuals at a meeting often involves a presentation. Office 365’s PowerPoint allows users to create, display, and disseminate information in formats ranging from the basic slide to animation to video.
Publisher: Sometimes communicating information to a broader audience requires something more permanent and more formal than a presentation at a meeting. The Publisher app in Office 365 provides users with the tools they need to publish professional-looking newsletters, brochures, and booklets.
OneNote: As the workforce has become more mobile, the need to capture information on the go has become increasingly important. Applications like OneNote allow users to take notes on any device and then retrieve those notes from any other device. It’s your basic productivity cloud app.
OneDrive: The other basic and fundamental cloud-based application is storage. With each Office 365 Business subscription, Microsoft provides users with up to 1TB of cloud storage in the form of an application called OneDrive for Business.
SharePoint: A subscription to Office 365 Business Premium also provides an enterprise with a few applications for backend infrastructure management. SharePoint, for example, can be used to host intranet websites for the enterprise. It also can be used to host smaller sites designed for smaller teams or divisions. The permissions for these sites can be designated by the users themselves or by appointed administrators.
Exchange: Each Office 365 for Business subscription includes an Exchange Server, which handles all the email management duties. By default, each user is granted 50GB of storage for email. Maintenance of the Exchange Server is generally handled at the administrator level.
Collaboration tools: Along with the typical productivity applications, Office 365 includes many collaboration tools—like Delve, Skype, Yammer, and Sway. These tools allow users to communicate, brainstorm ideas, share documents, and have video meetings while on the go.
Power BI: One of the most powerful tools any enterprise can have, regardless of size, is reliable business intelligence gathering applications. Office 365 for Business, through its Power BI application, provides enterprises with a set of tools for collecting, sorting, and presenting business intelligence data.
Infrastructure: All Office 365 subscriptions include a reliability guarantee of 99.9% uptime. In addition, permissions for internal access control are handled by administrators designated by the enterprise using tools supplied by Active Directory. Each Office 365 subscription includes five layers of security and proactive monitoring to help safeguard your data.
Collaboration and communication are the key components of productivity in the modern enterprise, and productivity is the lifeblood of the enterprise. Microsoft Office 365 provides the tools necessary to bring collaboration and communication—and by extension, productivity—to each individual in an enterprise.
For many companies, Office 365 is the de facto standard for productivity software. The performance of all competing products is generally measured against applications from the Office 365 suite.
Just about every knowledge worker in every enterprise is required to have an email account and a calendar application. Beyond that, most individuals in an enterprise will need to use, at least once in a while, a word processor. And a significant number of individuals in an enterprise will also find themselves needing to use presentation software or a spreadsheet at some point in their career.
These are the productivity tools of any enterprise. These are the tools used to get work done. That means Office 365 is important to just about every working individual.
Microsoft Office 365 is available right now. The current subscription includes applications updated to the Office 2016 versions. Of course, the key to the subscription model is that each user will always be using the most current and most secure version of each application because each application is continuously updated.
Enterprises with fewer than 300 users can purchase a subscription to Office 365 and download the appropriate applications via the Microsoft website. The Premium version costs $12.50 per user per month ($150/year). There are also versions of Office 365 available for individuals ($69.99/year) and households ($99.99/year).
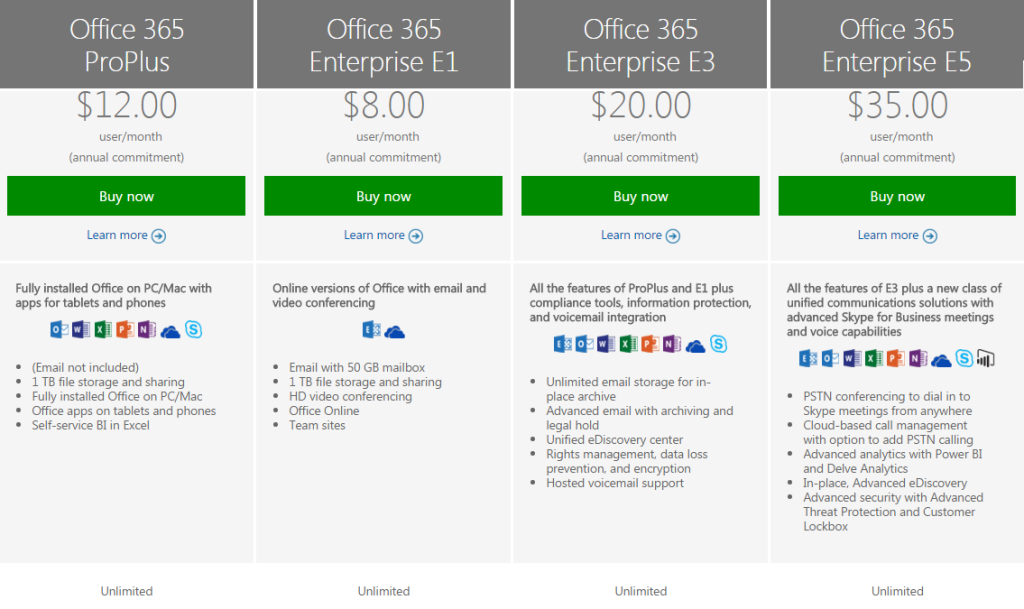
For large enterprises, unlimited user versions of Office 365 are available, ranging from $12 per person per month to $35 per person per month. Each subscription caters to a particular type of enterprise. More expensive enterprise versions of Office 365 add features like voicemail, compliance auditing, rights management, encryption, and Advanced Threat Protection.
Get answers from Microsofts Cloud Solutions Partner!
Call us at: 856-745-9990 or visit: https://southjerseytechies.net/
South Jersey Techies, LL C is a full Managed Web and Technology Services Company providing IT Services, Website Design Services, Server Support, Network Consulting, Internet Phones, Cloud Solutions Provider and much more. Contact for More Information.
To read this article in its entirety click here.
Exclusive offer from: BigBeagle.com | 24/7 Support: 8885051532
BigBeagle is a reseller of GoDaddy and offers GoDaddy products at a discounted price. Don’t forget to visit our coupon page at http://bigbeagle.com/coupons for the latest and greatest promotions.
*Some limitations apply. Applicable to new purchases only. Enter promo code into shopping cart to see full details. Offer expires Wednesday, June 14, 2017 at midnight (Mountain Time).
Copyright © 2017 BigBeagle.com. All rights reserved.

Exclusive offer from: BigBeagle.com | 24/7 Support: 8885051532
BigBeagle is a reseller of GoDaddy and offers GoDaddy products at a discounted price. Don’t forget to visit our coupon page at http://bigbeagle.com/coupons for the latest and greatest promotions.
*Some limitations apply. Applicable to new purchases only. Enter promo code into shopping cart to see full details. Minimum purchase of $40 required. Offer expires Tuesday, July 11, 2017 at midnight (Mountain Time).
Copyright © 2017 BigBeagle.com. All rights reserved.

Exclusive offer from: BigBeagle.com | 24/7 Support: 8885051532
Amit Shah — Customer Number: 57156051
BigBeagle is a reseller of GoDaddy and offers GoDaddy products at a discounted price. Don’t forget to visit our coupon page at http://bigbeagle.com/coupons for the latest and greatest promotions.
*Some limitations apply. Applicable to new purchases only. Enter promo code into shopping cart to see full details. Minimum purchase of $40 required. Offer expires Wednesday, November 16, 2016 at midnight (Mountain Time).
Copyright © 2016 BigBeagle.com. All rights reserved.

Exclusive offer from: BigBeagle.com | 24/7 Support: 8885051532
BigBeagle is a reseller of GoDaddy and offers GoDaddy products at a discounted price. Don’t forget to visit our coupon page at http://bigbeagle.com/coupons for the latest and greatest promotions.
*Some limitations apply. Applicable to new purchases only. Enter promo code into shopping cart to see full details. Minimum purchase of $20 required. Offer expires Wednesday, July 19, 2017 at midnight (Mountain Time).
Copyright © 2017 BigBeagle.com. All rights reserved.

