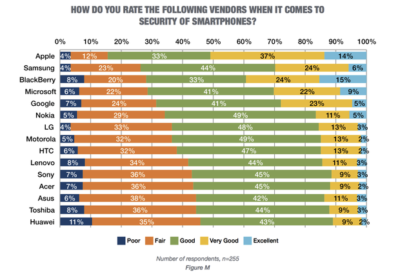
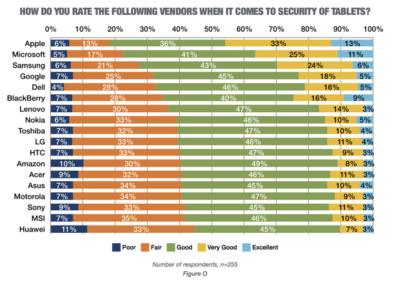
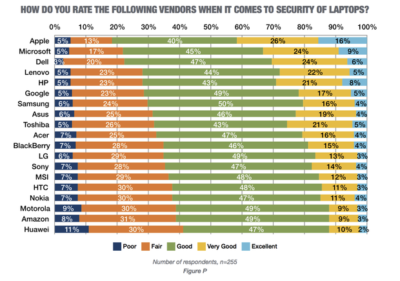
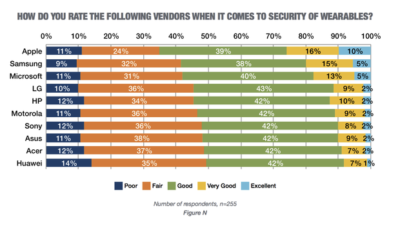
As ransomware increasingly targets healthcare organizations, schools and government agencies, security experts offer advice to help IT leaders prepare and protect.
Nigerian princes are no longer the only menaces lurking in an employee’s inbox. For healthcare organizations, schools, government agencies and many businesses, ransomware attacks—an especially sinister type of malware delivered through spear phishing emails that locks up valuable data assets and demands a ransom to release them—are a rapidly-growing security threat.
“We’re currently seeing a massive explosion in innovation in the types of ransomware and the ways it’s getting into organizations,” says Rick McElroy, security strategist for cyber security company Carbon Black Enterprise Response. “It’s a big business, and the return on investment to attackers is there—it’s going to get worse.”
While ransomware has existed for years, 2015 saw a spike in activity. The FBI received 2,453 complaints, with losses of over $1.6 million, up from 1,402 complaints the year before, according to annual reports from the bureau’s Internet Crime Complaint Center. And the numbers are only growing in 2016, the FBIreports.
“The Dark Web and Bitcoin allow almost anyone to sell stolen data without identification—cyber criminals understand they can make easy cash without the risk of being jailed,” says Ilia Kolochenko, CEO of web security company High-Tech Bridge. And hackers—most of which are located in developing countries—are growing more sophisticated, even developing downloadable ransomware toolkits for less-experienced hackers to deploy, according to the 2016 Institute for Critical Infrastructure Technology Ransomware Report.
“The days of grammatically incorrect, mass spam phishing attacks are pretty much over,” says James Scott, senior fellow and co-founder of the Institute for Critical Infrastructure Technology, and co-author of the report. Hackers can now check a victim’s social media accounts, and create a fake email address pretending to be a friend or contact in order to get them to click on an infected link or attachment. “It’s much more targeted, and will exploit a particular vulnerability in a device, application, server or software,” Scott adds.
A typical ransom demand is $300, according to a report from security firm Symantec.
Health threats
The healthcare sector is highly targeted by hacker attacks, due to antiquated or misconfigured computer security systems and the amount of sensitive data they hold, says David DeSanto, director of projects and threat researcher at Spirent Communications.
The large number of employees at most hospitals also makes cyber security safety training difficult, DeSanto says. Experts commonly see attacks occur through spear phishing—targeted emails with attachments with names such as “updated patient list,” “billing codes” or other typical hospital communications that employees may click on if not warned.
In 2015, over 230 healthcare breaches impacted the records of 500-plus individuals, according to data from the U.S. Department of Health and Human Services Office for Civil Rights.
A February ransomware attack launched against Hollywood Presbyterian Medical Center in southern California locked access to certain computer systems and left staff unable to communicate electronically for 10 days. The hospital paid a $17,000 ransom in bitcoin to the cybercriminals, says CEO Alan Stefanek.
Following security best practices can help healthcare organizations protect themselves. “The best way is to make regular backups of all systems and critical data so that you can restore back to a known good state prior to the ransomware being on the system,” DeSanto says.
Without security best practices, healthcare organizations may be left with few options to retrieve information. In these cases, healthcare organizations may choose to pay the ransomware fee. Some make enough money that paying the ransom for a few infected computers is low compared to the cost of maintaining the infrastructure to protect these attacks, DeSanto adds.
Schools and businesses
Hackers are gaining traction and using new methods across other industry verticals as well. In 2014, a large European financial services company (whose name was not disclosed) discovered with the help of High-Tech Bridge that a hacker placed a back door between a web application and a data set.
For six months, the hacker encrypted all information before it was stored in a database, undetected by company staffers. Then, they removed the encryption key, crashing the application, and demanded $50,000 to restore access to the database.
However, the company did not end up paying, thanks to mistakes made by the hackers, Kolochenko says.
Other victims are not as lucky, says Engin Kirda, professor of computer science at Northeastern University. “If the ransomware hacker does the encryption well, once the data is encrypted it’s nearly impossible to decrypt,” he adds.
Such was the case for South Carolina’s Horry County School District this February, when hackers froze networks for 42,000 students and thousands of staff. District technology director Charles Hucks tried to shut down the system, but within minutes, the attackers immobilized 60 percent of Horry County’s computers. The district paid $8,500 in Bitcoin to unlock their systems.
Tips for IT leaders
To prevent a ransomware attack, experts say IT and information security leaders should do the following:
- Keep clear inventories of all of your digital assets and their locations, so cyber criminals do not attack a system you are unaware of.
- Keep all software up to date, including operating systems and applications.
- Back up all information every day, including information on employee devices, so you can restore encrypted data if attacked.
- Back up all information to a secure, offsite location.
- Segment your network: Don’t place all data on one file share accessed by everyone in the company.
- Train staff on cyber security practices, emphasizing not opening attachments or links from unknown sources.
- Develop a communication strategy to inform employees if a virus reaches the company network.
- Before an attack happens, work with your board to determine if your company will plan to pay a ransom or launch an investigation.
- Perform a threat analysis in communication with vendors to go over the cyber security throughout the lifecycle of a particular device or application.
- Instruct information security teams to perform penetration testing to find any vulnerabilities.
Mitigating an attack
If your company is hacked with ransomware, you can explore the free ransomware response kit for a suite of tools that can help. Experts also recommend the following to moderate an attack:
- Research if similar malware has been investigated by other IT teams, and if it is possible to decrypt it on your own. About 30 percent of encrypted data can be decrypted without paying a ransom, Kolochenko of High-Tech Bridge says.
- Remove the infected machines from the network, so the ransomware does not use the machine to spread throughout your network.
- Decide whether or not to make an official investigation, or pay the ransom and take it as a lesson learned.
“There is always going to be a new, more hyper-evolved variant of ransomware delivered along a new vector that exploits a newly-found vulnerability within a common-use application,” Scott of ICIT says. “But there are so many technologies out there that offer security—you just have to use them.”
Have questions?
Get answers from Microsofts Cloud Solutions Partner!
Call us at: 856-745-9990 or visit: https://southjerseytechies.net/
South Jersey Techies, LL C is a full Managed Web and Technology Services Company providing IT Services, Website Design Services, Server Support, Network Consulting, Internet Phones, Cloud Solutions Provider and much more. Contact for More Information.
To read this article in its entirety click here.