Windows 8.1 will be released on October 17, 2013, followed by a full launch on October 18, 2013. Although Windows 8.1 is not a “new” operating system, the major updates created for 8.1 have made the upgrade more than a simple service pack.
Enterprise Benefits:
1. Mobility
Windows 8.1 benefits a wider range of employees to include a combination of productivity and mobility. IT can manage Windows 8.1 devices, such as desktops, laptops, and tablets, with a universal management client.
2. Tablets
Enabled hardware for Windows 8 offers the option to have a standard operating system for enterprises, but allow individual users to select their device, such as desktops, laptops, and tablets, and have a consistent interface across these devices.
3. Application Development
Streamlining Windows 8.1 allow developers to design applications that can work across devices, such as desktops, laptops, tablets and smartphones.
4. IT Support
To reduce the strain on IT resources for business mobility, standardizing on Windows 8.1 allows a majority of IT support to become simplified.
5. Total Savings
Standardizing on Windows 8.1 will reduce the cost for development, maintenance and support. Also, reducing costs by eliminating licensing/support costs of a enterprise environment with varied devices.
6. Restore Optimization
Windows 8.1 has the ability to restore factory settings for the operating system. For all businesses, this is an advantage and a simple way to reduce costs and recover time for IT departments.
7. IT Operations
Windows 8.1 is a services pack for Windows 8 that includes new features, not just fixes. Creating user documentation can be streamlined for Windows 8.1 for all applications. Additionally, future service packs will follow in the footsteps of Windows 8.1 to include new features; then IT departments can frequently provide updates to user documentation.
8. Reduced Confusion
To reduce user confusion, after a user joins to Windows Intune Management Service the user gains access to the Company Portal. The company portal has access to the applications, data, and device settings. Also, users can troubleshoot their own devices using the service desk self-help portal.
9. Security
Microsoft is enhancing security with Windows 8.1 with Remote Business Data Removal and the new Internet Explorer. Remote Business Data Removal provides control over encrypted data that can be wiped from any device. The new Internet Explorer has Anti-Malware included to scan binary extensions to prevent infections.
10. Education
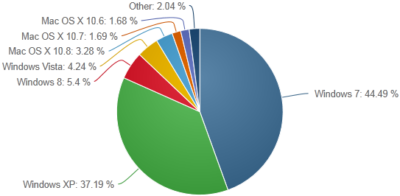
Windows 8.1 offers an evaluation of current infrastructure, how to execute migrations plans and ways to educate users on how to use the new version. Microsoft ends support for Windows XP on April 8, 2014, business should consider the option of upgrading to Windows 8.1.
For more information regarding Windows 8.1 click here.