Anna Kournikova (2001)
The Anna Kournikova virus is so named because it tricked its recipients into thinking they were downloading a sexy picture of the tennis star. Financial damages associated with Kournikova were limited, but the virus had a big pop culture impact: It became a plot point in a 2002 episode of the sitcom Friends.
Sasser (2004)
In April 2004, Microsoft issued a patch for a vulnerability in Windows’ Local Security Authority Subsystem Service (LSASS). Shortly after, a teenager in Germany released the Sasser worm to exploit the vulnerability in unpatched machines. Multiple variants of Sasser took out airline, public transportation, and hospital networks, causing $18 billion in damage.
Skulls.A (2004)
The Skulls.A is a legitimately spooky mobile trojan that affected the Nokia 7610 smartphone and other SymbOS devices. The malware was designed to change all icons on infected phones to Jolly Rogers and disable all phone functions, save for making and receiving calls.
F-Secure says Skulls.A caused little damage, but the trojan is undeniably creepy.
Zeus (2009)
While many malware programs on this list are little more than nuisances, Zeus (AKA Zbot) was a tool used by a complex criminal enterprise.
The trojan uses phishing and keylogging to steal online banking credentials, draining a cumulative $70 million from the accounts of its victims.
Melissa (1999)
Named after a Florida stripper, the Melissa virus was designed to propagate by sending itself to the first 50 contacts in its victims’ e-mail Outlook address book. The attack was so successful that the virus infected 20 percent of the world’s computers, causing an estimated $80 million in damage.
Virus creator David L. Smith (shown) was caught by the FBI, served 20 months in jail, and paid a $5,000 fine.
Sircam (2001)
Like many early malware scripts, Sircam used social engineering to trick people into opening an email attachment.
The worm chooses a random Microsoft Office file on victims’ computers, infects it, and sends it to all the people in the victims’ email contact list. A University of Florida study pegged Sircam cleanup costs at $3 billion.
Stuxnet (2009)
Stuxnet is one of the first known viruses created for cyberwarfare. Created in a joint effort between Israel and the U.S., Stuxnet targeted nuclear enrichment systems in Iran.
Infected computers instructed nuclear centrifuges to physically spin until they broke, all while providing fake feedback that operations were normal.
SQL Slammer/Sapphire (2003)
Taking up just 376 bytes, the SQL Slammer worm packed a lot of destruction into a tiny package. The worm slowed down the Internet, disabled 911 call centers, took down 12,000 Bank of America ATMs, and caused much of South Korea to go offline. It also crashed the network at Ohio’s Davis-Besse nuclear power plant.
Storm Trojan (2007)
Storm Trojan is a particularly sinister piece of email-distributed malware that accounted for 8 percent of all global infections just three days after its January 2007 launch.
The trojan created a massive botnet of between 1 and 10 million computers, and because it was designed to change its packing code every 10 minutes, Storm Trojan proved incredibly resilient.
Code Red (2001)
The Code Red worm, named after the Mountain Dew flavor preferred by its creators, infected up to one-third of all Microsoft ISS web servers upon release.
It even took down whitehouse.gov, replacing its homepage with a “Hacked by Chinese!” message. Estimated damages due to Code Red were in the billions of dollars worldwide.
Nimda (2001)
Released just after the 9/11 attack, many thought the devastating Nimda worm had an Al Qaeda connection (never proven).
It spread via multiple vectors, bringing down banking networks, federal courts and other key computer systems. Cleanup costs for Nimda exceeded $500 million in the first few days alone.
ILOVEYOU (2000)
The ILOVEYOU worm, AKA Love Letter, disguised itself in email inboxes as a text file from an admirer.
But this Love Letter was anything but sweet: In May 2000, it quickly spread to 10 percent of all Internet-connected computers, leading the CIA to shut down its own email servers to prevent its further spread. Estimated damages were $15 billion.
Cryptolocker (2014)
Computers infected with Cryptolocker have important files on their hard drives encrypted and held at ransom. Those who pay approximately $300 in bitcoin to the hackers are given access to the encryption key; those who fail to pay have their data deleted forever.
Netsky (2004)
The Netsky worm, created by the same teen who made Sasser, made its way around the world by way of email attachments. The P variant of Netsky was the most widespread worm in the world even more than two years after its February 2004 launch.
Conficker (2008)
The Conficker worm (AKA Downup, Downadup, Kido), first detected in December 2008, was designed to disable infected computers’ anti-virus programs and block autoupdates that may otherwise remove it from computers.
Conficker quickly spread to numerous important computer networks, including those of the English, French, and German armed forces, causing $9 billion in damage.
Michaelangelo (1992)
The Michelangelo virus itself spread to relatively few computers and caused little real damage. But the concept of a computer virus set to “detonate” on March 6, 1992 caused a media-fueled mass hysteria, with many afraid to operate their PCs even on anniversaries of the date.
Sobig.F (2003)
The Sobig.F trojan infected an estimated 2 million PCs in 2003, grounding Air Canada flights and causing slowdowns across computer networks worldwide. This tricky bug-in-disguise cost $37.1 billion to clean up, making it one of the most expensive malware recovery efforts in history.
MyDoom (2004)
In September 2004, TechRepublic called MyDoom “the worst virus outbreak ever,” and it’s no surprise why. The worm increased the average page load time on the Internet by 50 percent, blocked infected computers’ access to anti-virus sites, and launched a denial-of-service attack on computing giant Microsoft.
The worldwide costs associated with cleanup of MyDoom is estimated to be just shy of $40 billion.
Have questions?
Get help from IT Experts/Microsofts Cloud Solutions Partner
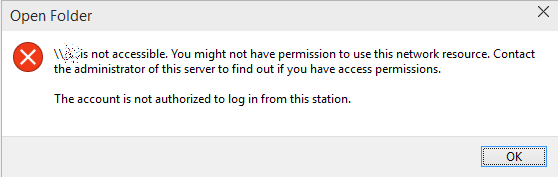
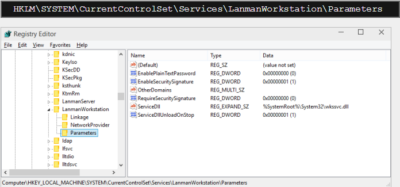
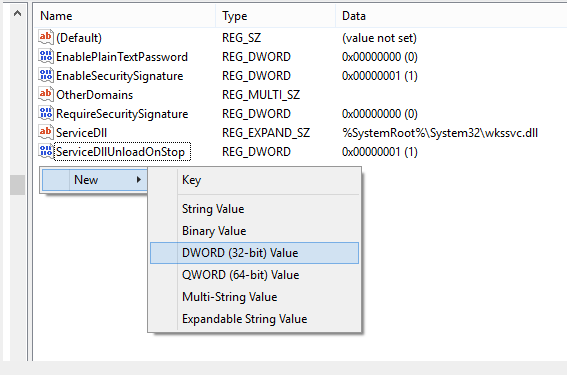
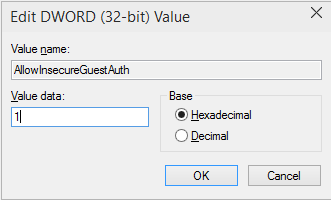
Call us at: 856-745-9990 or visit: https://southjerseytechies.net/
South Jersey Techies, LLC is a full Managed Web and Technology Services Company providing IT Services, Website Design Services, Server Support, Network Consulting, Internet Phones, Cloud Solutions Provider and much more. Contact for More Information.
To read this article in its entirety click here.