Microsoft Outlook can connectivity issue with Microsoft Exchange. Troubleshooting and fixing these issues can range from a simple reboot to creating a new mail profile.
Restart Outlook and/or Computer
Many connectivity problems with Outlook can be resolved by simply restarting Outlook and/or the Computer.
- Restart Outlook.
- After restarting Outlook, verify connectivity.
- If there are still connectivity problems, restart Computer.
- Once computer is up and running, verify connectivity in Outlook.
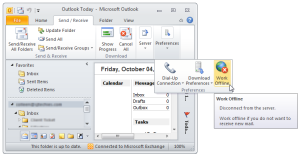
Offline Mode
Outlook 2010 and newer:
- Click the Send/Receive tab.
- Locate the Work Offline button.
- Click the Offline button.
Outlook 2007 and older:
- Click File Menu.
- Uncheck the Offline box.
At the bottom of your Outlook Window there will be a “Trying to Connect” prompt. If Outlook is “Connected” the problem is solved.
Rebuild PST or OST File
OST File
- Close Outlook.
- Open the Control Panel.
- Select Mail icon.
- In the next window, click Data Files.
- Locate your data file, select and click Open File Location.
- Locate the data file using Windows Explorer.
- Rename the file extension from .OST to .OLD.
- Close these windows and open Outlook.
PST File
- Search for scanpst.exe using Windows Explorer.
- Double click scanpst.exe to run the application.
- In the next window, click Browse.
- Locate your .pst file.
- Click Start.
- Scanpst will scan the data file eight times.
- If the scan finds errors, there will be a prompt to repair. For backup purposes, check the Make Backup Of Scanned File Before Repairing box.
- Click Repair.
- Close these windows and open Outlook.
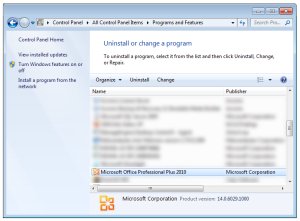
Repair Software Install
- Open Control Panel.
- Click Programs and Features.
- Scroll down and highlight the Microsoft Office installation.
- Click Change.
- Select Repair.
- Click Continue.
- Allow the repair to complete.
- Reboot your computer.
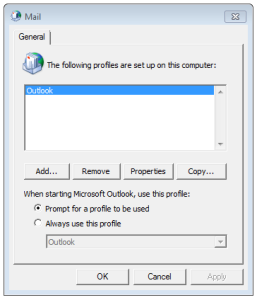
Recreate Mail Profile
- Open Control Panel.
- Click Mail.
- Select Show Profiles.
- Click Add.
- Name the new profile.
- Follow the steps for the Outlook Account Setup Wizard.
- Verify the new profile and set as the default or delete old profile.