Microsoft Word
Sorting data in a Word document isn’t something you routinely do. On the other hand, presenting list and table data is, so the potential exists that one day you’ll want to sort something. The good news is that it’s easy to sort data in a table or a list. In this article, I’ll show you how to do just that. We’ll work through a few simple sorting examples. You can use most any table, or you can download the example .docx or .doc file.
Behind the scenes
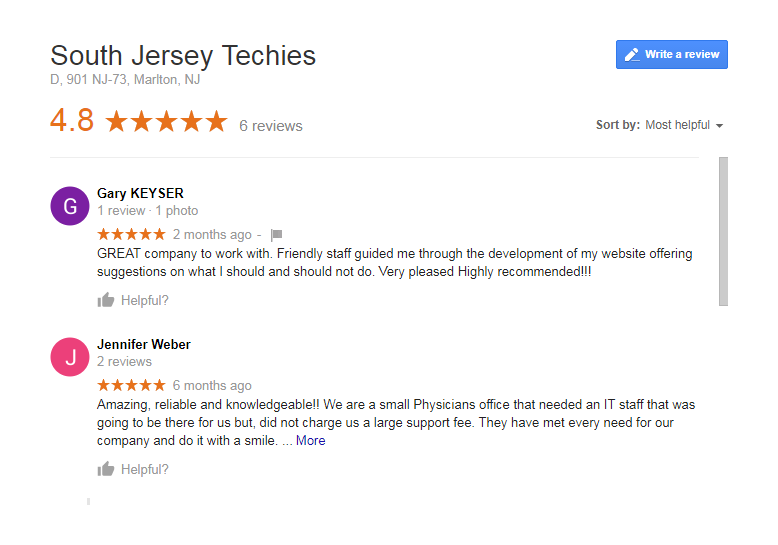
Word relies on paragraphs when sorting, which seems a bit odd within the context of a table (or list). The paragraph formatting mark determines where one paragraph ends and the next starts. As you can see in Figure A, there’s no paragraph mark in a table. The end-of-cell markers denote the end of each cell’s content. The similar marker at the end of each row (outside the right border) is an end-of-row marker. These markers also contain cell and row formatting. When sorting a table, Word relies on the end-of-row marker to identify where one row ends and the next begins, the same way the paragraph mark does. (To see a document’s formatting symbols, click Show/Hide in the Paragraph group on the Home tab.)
Figure A
Sort by the first column
We’ll start with the simplest sort possible; we’ll sort a table by the values in the first column. To do so, select, the table by clicking its move handle (the small square in the top-left corner). If you don’t see this handle, check the view. It’s available only in Print Layout and Web Layout. With the entire table selected, do the following:
- Click the contextual Layout tab. In the Data group, click Sort — or click Sort in the Paragraph group on the Home tab. In Word 2003, choose Sort from the Table menu.
- The resulting dialog does a good job of anticipating the sort. Notice that the Header Row option (at the bottom) is selected. As a result, the Sort By field is set to Species — the label in the first column’s header (Figure B).
Figure B - This is exactly what we want, so click OK. Figure C shows the sorted table.
Figure C
Before we move on, let’s discuss the Type and Using options to the right. We didn’t need to change either, but sometimes you will. The Type options are Text, Number, and Date. Word usually defaults to the appropriate data type. You can force a specific type by choosing a different option other than the one Word assumes (but you’ll rarely have reason to do so). The Using options defaults to Paragraph — we talked about that earlier.
Sort by the second column
That first exercise was easy. Let’s complicate things a bit by sorting by the second column. Fortunately, it’s just as easy as the first. Repeat steps 1 and 2 from the first exercise. Then, do the following:
- In the resulting dialog, click the Sort By drop-down.
- Choose Common Name, the header label for the second column.
- Click OK. Figure D shows the results of sorting by the second column.
Figure D
That wasn’t any more difficult that the first sort. Tell Word which column contains the values you want to sort by and click OK — that’s it!
Sort by multiple columns
With only two sort tasks under your belt, you’re beginning to see how simple the sorting process in Word can be. Let’s complicate things a bit so you can see how flexible this feature truly is. Let’s sort by the Class column and then sort the bird and mammal groups in a secondary sort. Repeat steps 1 and 2 from the first two exercises. Then, do the following:
- To sort by the Class, choose Class from the Sort By drop-down.
- To further sort each class group, click Common Name from the Then by drop-down (Figure E). You could add a third column to the sort if the results warranted the additional grouping.
Figure E - Click OK to see the results shown in Figure F.
Figure F
What about lists?
You might be wondering how to sort the same data in list form. Word handles the list sort the same way — the exact same way. Highlight the list and click Sort in the Paragraph group on the Home tab. In the resulting dialog, check the header option and set appropriately (if necessary). Then, determine the sort order by choosing the fields (columns), appropriately.Figure G shows the result of sorting the same data in list form.
Figure G
Sort a columnar list the same way you sort a table.