Bring your Big BOLD business ideas to light!
Save up to 15% off of your order.
(5% off $35, 10% off $55 and 15% off $85)

Visit: www.bigbeagle.com
Offer expires Sunday, October 6, 2013.
(5% off $35, 10% off $55 and 15% off $85)

Offer expires Sunday, October 6, 2013.
(5% off $30, 10% off $70 and 15% off $100)

Offer expires Sunday, November 3, 2013.

Promo code rsa1151a. Offer expires Sunday, November 17, 2013.

Promo code rsa1152a. Offer expires Sunday, December 1, 2013.

Promo code rsa1153a. Offer expires Sunday, December 15, 2013.
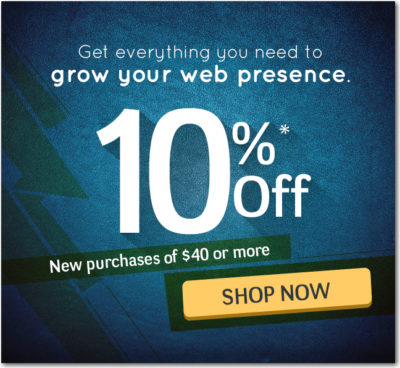
Promo code: rd15214a. Offer expires Sunday, February 9, 2014.
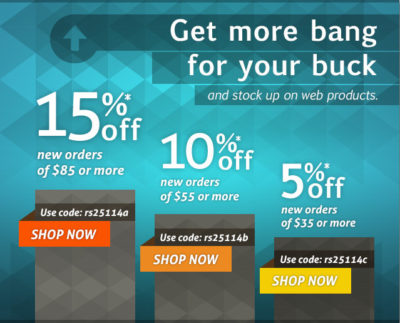
Offer expires Sunday, February 23, 2014.

