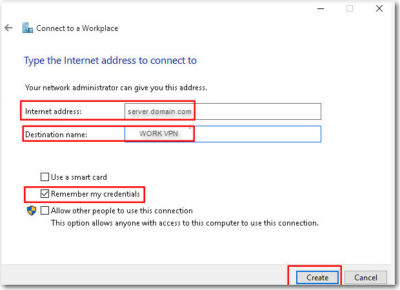
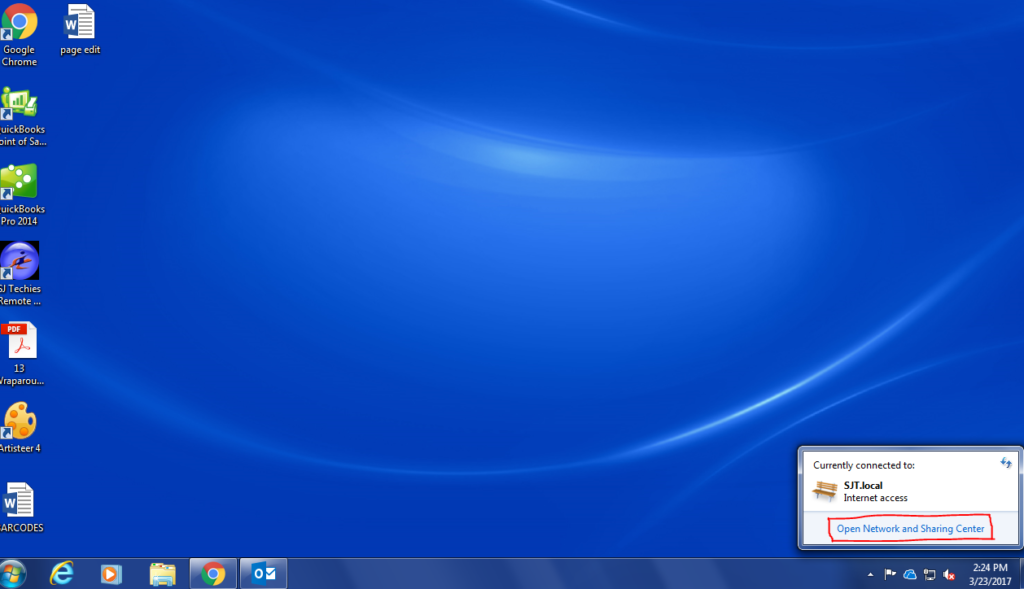
Consumers are not the only ones vulnerable to scams. If you own a small business or are part of a nonprofit organization, you could be open to several different types of cons without even realizing it.
The Federal Trade Commission (FTC) has put together a list of some of the more common scams and posted them on the website along with plenty of resources to help you spot con artists and keep them from taking advantage of you and your business.
“Your best protection? Learn the signs of scams that target businesses,” the FTC says. “Then tell your employees and colleagues what to look for so they can avoid scams.”
From the FTC website:
Fake Invoices
Scammers create phony invoices that look like they’re for products or services your business uses — maybe office or cleaning supplies or domain name registrations. Scammers hope the person who pays your bills will assume the invoices are for things the company actually ordered. Scammers know that when the invoice is for something critical, like keeping your website up and running, you may pay first and ask questions later. Except it’s all fake and if you pay, your money may be gone.
Unordered Office Supplies and Other Products
Someone calls to confirm an existing order of office supplies or other merchandise, verify an address, or offer a free catalog or sample. If you say yes, then comes the surprise — unordered merchandise arrives at your doorstep, followed by high-pressure demands to pay for it. If you don’t pay, the scammer may even play back a tape of the earlier call as “proof” that the order was placed. Keep in mind that if you receive merchandise you didn’t order, you have a legal right to keep it for free.
Directory Listing and Advertising Scams
Con artists try to fool you into paying for nonexistent advertising or a listing in a nonexistent directory. They often pretend to be from the Yellow Pages. They may ask you to provide contact information for a “free” listing or say the call is simply to confirm your information for an existing order. Later, you’ll get a big bill, and the scammers may use details or even a recording of the earlier call to pressure you to pay.
Utility Company Imposter Scams
Scammers pretend to call from a gas, electric, or water company saying your service is about to be interrupted. They want to scare you into believing a late bill must be paid immediately, often with a wire transfer or a reloadable card or gift card. Their timing is often carefully planned to create the greatest urgency — like just before the dinner rush in a restaurant.
Government Agency Imposter Scams
Scammers impersonate government agents, threatening to suspend business licenses, impose fines, or even take legal action if you don’t pay taxes, renew government licenses or registrations, or other fees. Some businesses have been scared into buying workplace compliance posters that are available for free from the U.S. Department of Labor. Others have been tricked into paying to receive nonexistent business grants from fake government programs. Businesses have received letters, often claiming to be from the U.S. Patent and Trademark Office, warning that they’ll lose their trademarks if they don’t pay a fee immediately, or saying that they owe money for additional registration services.
Tech Support Scams
Tech support scams start with a call or an alarming pop-up message pretending to be from a well-known company, telling you there is a problem with your computer security. Their goal is to get your money, access to your computer, or both. They may ask you to pay them to fix a problem you don’t really have, or enroll your business in a nonexistent or useless computer maintenance program. They may even access sensitive data like passwords, customer records, or credit card information.
Social Engineering, Phishing and Ransomware
Cyber scammers can trick employees into giving up confidential or sensitive information, such as passwords or bank information. It often starts with a phishing email, social media contact, or a call that seems to come from a trusted source, such as a supervisor or other senior employee, but creates urgency or fear. Scammers tell employees to wire money or provide access to sensitive company information. Other emails may look like routine password update requests or other automated messages but are actually attempts to steal your information. Scammers also can use malware to lock organizations’ files and hold them for ransom.
Business Promotion and Coaching Scams
Some scammers sell bogus business coaching and internet promotion services. Using fake testimonials, videos, seminar presentations, and telemarketing calls, the scammers falsely promise amazing results and exclusive market research for people who pay their fees. They also may lure you in with low initial costs, only to ask for thousands of dollars later. In reality, the scammers leave budding entrepreneurs without the help they sought and with thousands of dollars of debt.
Changing Online Reviews
Some scammers claim they can replace negative reviews of your product or service, or boost your scores on ratings sites. However, posting fake reviews is illegal. FTC guidelines say endorsements — including reviews — must reflect the honest opinions and experiences of the endorser.
Credit Card Processing and Equipment Leasing Scams
Scammers know that small businesses are looking for ways to reduce costs. Some deceptively promise lower rates for processing credit card transactions, or better deals on equipment leasing. These scammers resort to fine print, half-truths, and flat-out lies to get a business owner’s signature on a contract. Some unscrupulous sales agents ask business owners to sign documents that still have key terms left blank. Don’t do it. Others have been known to change terms after the fact. If a sales person refuses to give you copies of all documents right then and there — or tries to put you off with a promise to send them later — that could be a sign that you’re dealing with a scammer.
Fake Check Scams
Fake check scams happen when a scammer overpays with a check and asks you to wire the extra money to a third party. Scammers always have a good story to explain the overpayment — they’re stuck out of the country, they need you to cover taxes or fees, you’ll need to buy supplies, or something else. By the time the bank discovers you’ve deposited a bad check, the scammer already has the money you sent them, and you’re stuck repaying the bank. This can happen even after the funds are made available in your account and the bank has told you the check has “cleared.”