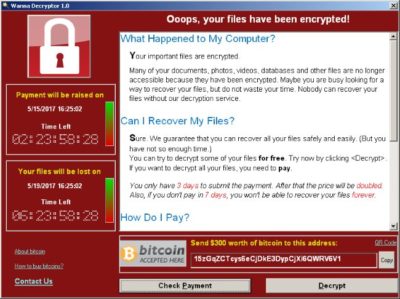
The hackers used “ransomware” to lock the hospital out of its own medical records.
Not all kidnappers grab your loved ones.
A growing online threat – ransomware – essentially abducts your computer system, putting data and services off-limits to users and demanding a payment to restore access.
“We are seeing more cases of this – sometimes almost on a daily basis,” said New Jersey State Police Capt. Steve Jones. “And we’re not seeing all of it, because people may be too embarrassed or don’t believe it can be helped.”
Ransomware viruses are a plague. Once infected — installed to your computer by a website you’ve visited, a rogue email attachment or link, or instant message — your computer will lock up. With names like CryptoWall, these types of viruses may create a popup window or Web page warning you that you’ve broken some law and have to pay a fine, anywhere from hundreds to thousands of dollars, according to the FBI.
These scams threaten to encrypt your files forever or destroy them unless a ransom is paid, according to the FBI.
Once paid, your computer is unlocked or a code is sent to unlock the machine, authorities said.
Between April 2014 and June 2015, the FBI received 992 CryptoWall-related complaints with victims reporting a loss of more than $18 million.
The state’s top cybersecurity unit recently launched an online effort to help people guard against ransomware.
“For many organizations, preventing ransomware entirely is nearly impossible,” says the New Jersey Cybersecurity and Communications Integration Cell (NJCCIC), which introduced a Ransomware Threat Profile page at its website in February.
But it notes individuals and companies can take measures to prevent infections and to limit their impact.
Although ransomware can lock up laptops and desktop computers, the risk is particularly great for data-dependent organizations like hospitals and accounting firms, said Jones, the State Police spokesman.
So far, at least three hospitals have been hit nationwide – in California, Kentucky and the Washington, D.C., area. South Jersey hospitals are well aware of the menace.
“It’s a big concern. It’s something that has really spiked,” said Tom Handlon, chief information security officer for Kennedy Health, which operates three acute-care hospitals in South Jersey.
Handlon gave no details, but said Kennedy seeks to protect itself through protective measures inside its computer system and by promoting safe conduct by employees.
“We’re monitoring it constantly and updating as we go along,” he said. “We are really educating the staff and our entire organization that we are a target.”
A similar view came from Tom Rubino, spokesman for Cooper University Healthcare System in Camden.
“We have tracked the recent wave of ransomware attacks that have targeted hospitals across the nation,” Rubino said. He said Cooper’s IT security team “is proactively taking measures to prevent ransomware infection of our computer systems.”
“Additionally, as a critical component for preventing all computer viruses, we are increasing our employee education efforts.”
A key precaution is to back up your computer’s contents on a frequent basis, Jones said. “But you’ve got to keep the backup drives disconnected,” he warned. “Otherwise, the ransomware can migrate to the backups.”
The State Police in March 2015 investigated a hacking incident that disabled much of the computer system for the Swedesboro-Woolwich school system. In that case, a hacker demanded more than $125,000 in the form of a digital currency called bitcoins.
The district, which did not pay the ransom, had to wipe clean its email servers and cafeteria lunch-ordering system to rid itself of ransomware. Only a handful of classroom computers were infected.
Hackers exploited a gap in the district’s computer security system and a vendor’s “weak” passport to take over the computer system, Michael Procopio, Educational Information and Resource Center’s director of technology, said at the time. EIRC experts helped the district restore its system.
The district’s hacker was believed to have struck from abroad – a familiar pattern, according to the State Police.
“Many of these messages and attacks are coming through foreign servers,” Jones said. “The countries that house these servers are not often countries that have a real open relationship with law enforcement.”
Tools have been available to help decrypt older versions of ransomware, said Dave Weinstein, New Jersey’s director of cybersecurity.
“At this point, the strain has morphed to the point where there is no releasing your files,” said Al Della Fave, a spokesman for the Ocean County Prosecutor’s office. “The lock these cybercriminals put on your files is foolproof at this point.”
Unless you’ve backed up your computer prior to the infection, Della Fave said, “The only way you would get your files back is to pay.”
“Ransomware is working” for cyberthieves, said Ben Johnson, chief security strategist at Carbon Black Inc., a computer security firm in Waltham, Massachusetts. “People are paying.”
In the last few weeks, cybercriminals have come up with some new twists, he said. For instance, one version encrypts files more quickly after someone opens up a malware-filled Microsoft Word document or some other attachment.
Other versions encrypt the computer at its most basic level so it can’t even power on, or use the computer’s own system administration tools to infect itself, he said.
The best course of action is to make sure you don’t get the virus. “You must be super careful what you click on,” Della Fave said.
Here’s what you should do, according to Johnson and the Ocean County prosecutor’s office: