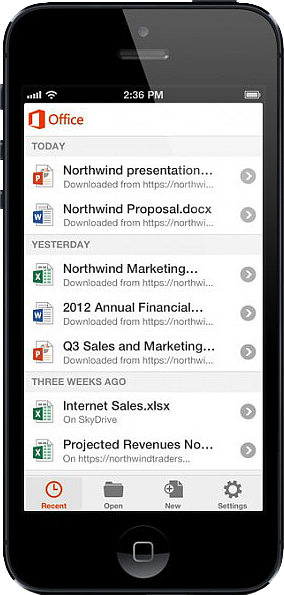
 On June 14, 2013, Microsoft released Office Mobile in the Apple Store for all Office 365 users at no cost. This app is available for iPhone 4 and up, iPad 3rd generation and up, iPad Mini and iPod Touch 5th generation. All devices are required to run iOS 6 and up.
On June 14, 2013, Microsoft released Office Mobile in the Apple Store for all Office 365 users at no cost. This app is available for iPhone 4 and up, iPad 3rd generation and up, iPad Mini and iPod Touch 5th generation. All devices are required to run iOS 6 and up.
Office Mobile allows you to view and edit Word, Excel, and PowerPoint documents. SkyDrive, SkyDrive Pro and SharePoint are ways to access documents. “Recent Documents” tracks the most recent documents that you viewed or changed and makes them easily accessible. Offline editing does not require a constant internet connection but allows you to save your changes once reconnected to a network.
On June 10, 2013 Apple announced that iWork Apps, such as Pages, Numbers and Keynote, can cross platforms to be used on Windows Systems. Although, iWork Apps are proficient, they can not compare to the Office Suite.
Microsoft has taken a huge step by crossing platforms with Office software and returning the upper hand to Microsoft. Office 365 has become more valuable for businesses and home users.
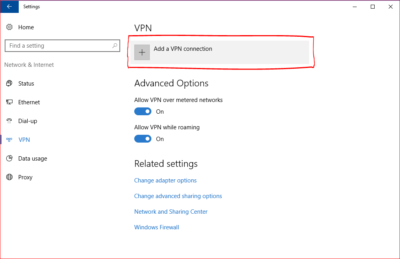
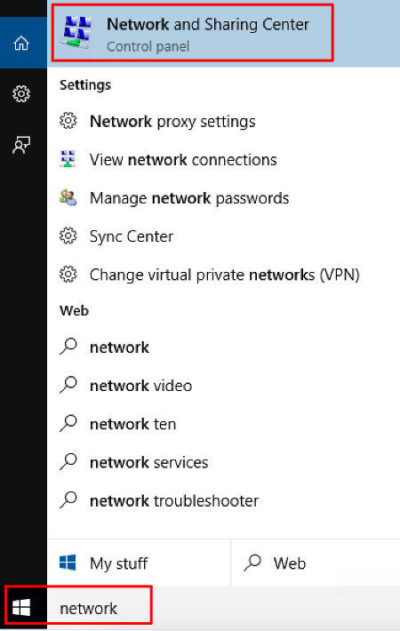
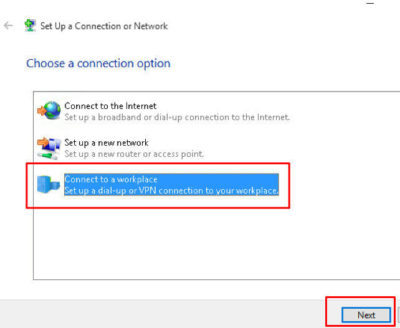
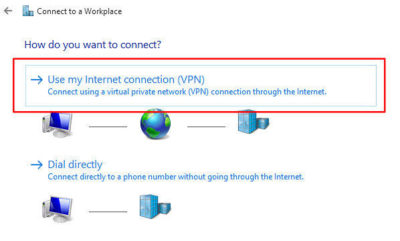
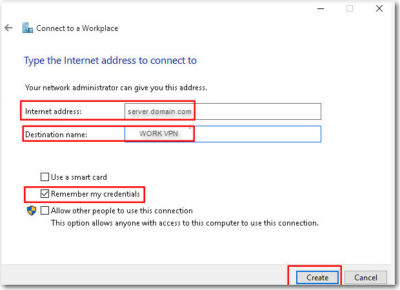
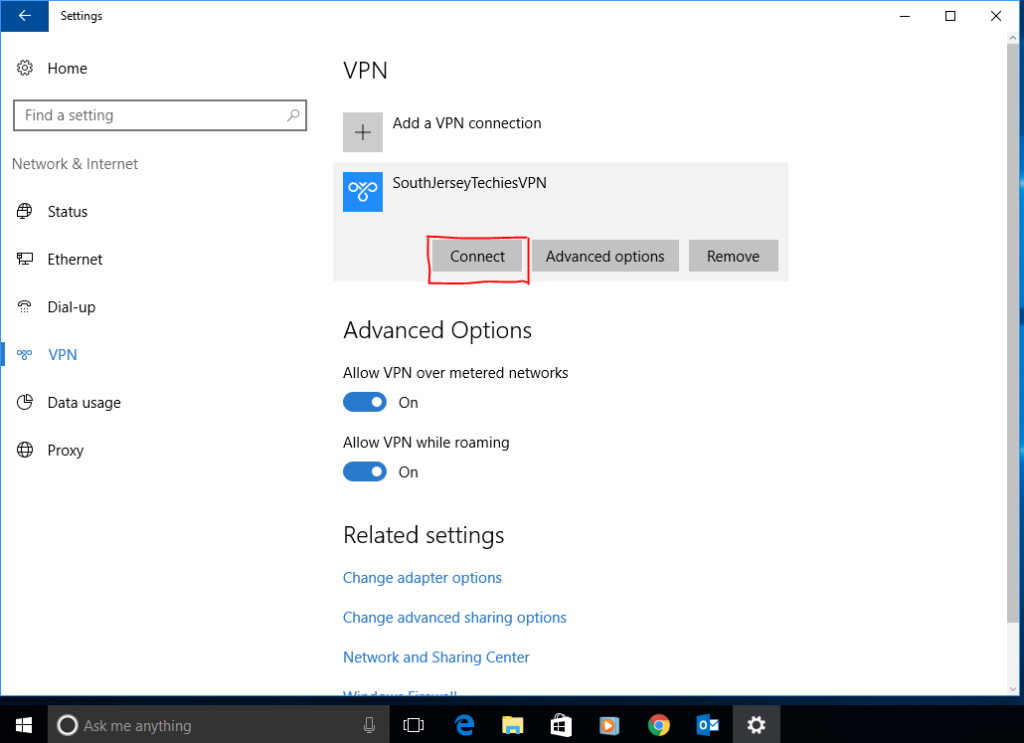
For more information on Hosted Services and Office 365
please contact us 856-745-9990 or click here.