What has happened?
On May 12, 2017 a new variant of the Ransom.CryptXXX ransomware family (detected as Ransom.Wannacry) began spreading widely, impacting a large number of organizations, particularly in Europe.
What is the WannaCry ransomware?
WannaCry encrypts data files and asks users to pay a US$300 ransom in bitcoins. The ransom note indicates that the payment amount will be doubled after three days. If payment is not made after seven days, the encrypted files will be deleted.
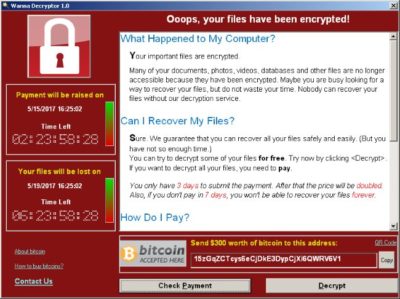
Figure 1. Ransom demand screen displayed by the WannaCry Trojan
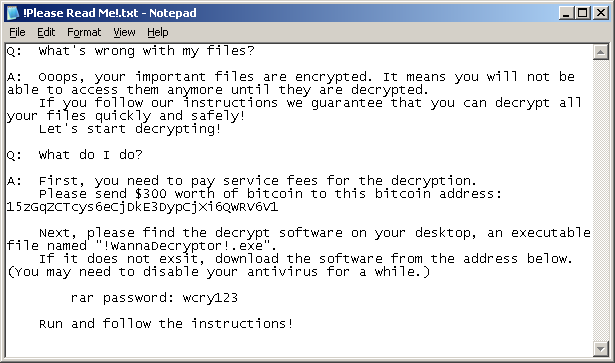
It also drops a file named !Please Read Me!.txt which contains the ransom note.
Figure 2. Ransom demand note from WannaCry Trojan
It propagates to other computers by exploiting a known SMB remote code execution vulnerability (MS17-010) in Microsoft Windows computers.
Are you protected against this threat?
South Jersey Techies, LLC recommends and offers Symantec Endpoint Protection to its clients. Symantec Endpoint Protection customers are protected against WannaCry using a combination of technologies: Antivirus, SONAR protection, Network-based protection.
All South Jersey Techies Managed IT Services client computers have the latest Windows security updates installed, in particular MS17-010, to prevent spreading. If your business / organization is not on our Managed IT Services plan please check or contact us to ensure that you have the latest updates installed.
Who is impacted?
A number of organizations globally have been affected, the majority of which are in Europe.
Is this a targeted attack?
No, this is not believed to be a targeted attack at this time. Ransomware campaigns are typically indiscriminate.
Can I recover the encrypted files?
Decryption is not available at this time but companies are investigating. South Jersey Techies, LLC does not recommend paying the ransom. Encrypted files should be restored from back-ups where possible. South Jersey Techies offers a number of backup solutions including Carbonite Online Backup and cloud storage solutions. If you are unsure about your computer / server backups, please check or contact us to discuss the best solution for your business.
What are best practices for protecting against ransomware?
- New ransomware variants appear on a regular basis. Always keep your security software up to date to protect yourself against them.
- Keep your operating system and other software updated. Software updates will frequently include patches for newly discovered security vulnerabilities that could be exploited by ransomware attackers.
- Email is one of the main infection methods. Be wary of unexpected emails especially if they contain links and/or attachments.
- Be extremely wary of any Microsoft Office email attachment that advises you to enable macros to view its content. Unless you are absolutely sure that this is a genuine email from a trusted source, do not enable macros and instead immediately delete the email.
- Backing up important data is the single most effective way of combating ransomware infection. Attackers have leverage over their victims by encrypting valuable files and leaving them inaccessible. If the victim has backup copies, they can restore their files once the infection has been cleaned up. However organizations should ensure that back-ups are appropriately protected or stored off-line so that attackers can’t delete them.
- Using cloud services could help mitigate ransomware infection, since many retain previous versions of files, allowing you to “roll back” to the unencrypted form.
Have additional questions?
Feel free to call us at contact us or (856) 745-9990 with any questions you may have.