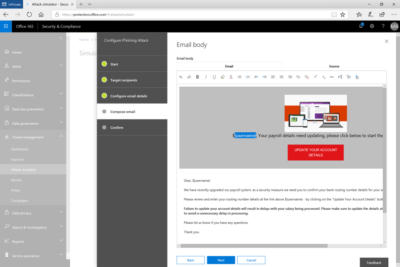
Admins can send simulated phishing and attack emails to find security and training weaknesses.
A few weeks ago, Microsoft released a public preview for Attack Simulator for Office 365 Threat Intelligence. On April 17th Microsoft announced that Attack Simulator is now generally available. Attack Simulator for Office 365 Threat Intelligence is available to all Office 365 E5 or Office 365 Threat Intelligence customers.
With Attack Simulator, customers can launch simulated attacks on their end users, determine how end users behave in the event of an attack, and update policies and ensure that appropriate security tools are in place to protect the organization from threats. The GA of Attack Simulator adds a new HTML editor so realistic looking HTML emails can be sent in simulations of spear-phishing. Also, two spear-phishing templates are available for immediate use in the spear phishing simulation.
Attack Simulator includes the three attack scenarios from our public preview.
Display Name Spear Phishing Attack: Phishing is the generic term for socially engineered attacks designed to harvest credentials or personally identifiable information (PII). Spear phishing is a subset of this phishing and is more targeted, often aimed at a specific group, individual, or organization. These attacks are customized and tend to leverage a sender name that generates trust with the recipient.
Password Spray Attack: To prevent bad actors from constantly guessing the passwords of user accounts, often there are account lockout policies. For example, an account will lockout after a certain number of bad passwords are guessed for a user. However, if you were to take a single password and try it against every single account in an organization, it would not trigger any lockouts. The password spray attack leverages commonly used passwords and targets many accounts in an organization with the hope that one of the account holder uses a common password that allows a hacker to enter the account and take control of it. From this compromised account, a hacker can launch more attacks by assuming the identity of account holder.
Brute Force Password Attack: This type of attack consists of a hacker trying many passwords or passphrases with the hope of eventually guessing correctly. The attacker systematically checks all possible passwords and passphrases until the correct one is found.
This video demonstrates how Attack Simulator can help organizations educate users to become more secure from cyber threats. With Attack Simulator, admins can train all their end users, and especially those who are attacked most often. This proactive training is a powerful way to ensure that your organization can prevent the impact from advanced threats. Over the coming months, more threat simulations will be added to Attack Simulator so organizations can simulate the most prevalent threat types from the modern threat landscape.
Experience the benefits of Attack Simulator for Office 365 Threat Intelligence by beginning an Office 365 E5 trial today. Also, learn more about how Microsoft leverages threat intelligence and the value of threat intelligence.


