Check out a recently developed and designed website by South Jersey Techies Website Team for Garden State Home Loans in Cherry Hill, NJ.

Check out a recently developed and designed website by South Jersey Techies Website Team for Garden State Home Loans in Cherry Hill, NJ.

Kon’nichiwa, hola, and bonjour says Google, as it expands Gmail calling to support a total of 38 languages and four currencies including Euros, British pounds and Canadian / US dolla dolla bills y’all. The calling feature allows Gmail users to call landlines and mobile phones from within their Gmail browser for next to nothing, making the email center a one-stop shop for IMs, emails, video and voice calls. The year-old service is lowering its call rates to $0.10 per minute to mobile phones in the UK, France, and Germany, $0.15 per minute to Mexico, and $0.02 per minute to any number in China and India. Calling landlines is even cheaper — which would be fantastic if you actually knew someone that still used one. The expanded language support and cheaper calls adds another piece of ammo to Google’s arsenal as it goes head-to-head with Skype (which charges $0.18 – $0.25 per minute for calls to UK mobile numbers), after the company conveniently partnered with Google+’s arch nemesis for calls from within the social network. But hey, at least those late-night arguments won’t cost the former nearly as much as it once did.
To view the original article in it’s entirety, Click Here.
In today’s digital age, cybersecurity is at the forefront of technology, both at the workplace and in our personal lives. With the increasing frequency and sophistication of cyber threats, it is essential that we all play a role in protecting sensitive information both business and personal.
To help you stay informed and vigilant about cybersecurity best practices, we have created a Quick Reference Guide for Cybersecurity to be shared with your users as a courtesy to better protect themselves from cyber threats and contribute to a safer digital environment.
Quick Reference CyberSecurity Guide
 RingCentral is a company that specializes in providing business VoIP services, fax services and mobile communication solutions. With plans ranging from a single user to over 20 users, RingCentral makes it clear that they can cater to both small businesses and large corporations. With a cloud-based virtual office system and new Interface, RingCentral makes it possible to enjoy your virtual office from virtually anywhere.
RingCentral is a company that specializes in providing business VoIP services, fax services and mobile communication solutions. With plans ranging from a single user to over 20 users, RingCentral makes it clear that they can cater to both small businesses and large corporations. With a cloud-based virtual office system and new Interface, RingCentral makes it possible to enjoy your virtual office from virtually anywhere.
![]() Using your RingCentral number and App from Google Play or iTunes, you will have unlimited texting to customers and co-workers from your Tablet or Smartphone.
Using your RingCentral number and App from Google Play or iTunes, you will have unlimited texting to customers and co-workers from your Tablet or Smartphone.
Boosting the efficiency of the RingCentral system, many features have been added, corrected and removed. The new interface is mapped with navigation tabs that can be used on a Computer, Tablet or Smartphone.
RingCentral Conferencing includes host and participant access codes for anytime conference calls. All users can invite and have up to 1000 attendees for a conferencing from their mobile devices.
RingCentral Presence feature allows you to see the status of colleagues on your phone. Whether on you desk phone or cell phone, Presence will tell you which lines are available, busy and on hold.

Google Chrome, Microsoft Edge, Mozilla Firefox and Apple’s Safari browser have all been impacted by a single zero-day vulnerability. The flaw, tracked as CVE-2023-4863, is caused by a heap buffer overflow in the WebP code library. Once exploited it can lead to system crashes and arbitrary code execution, where hackers can gain control over an infected device.
CVE-2023-4863 was first identified by researchers at The Citizen Lab, a research arm of the University of Toronto. The institution subsequently informed Google and Apple of the vulnerability’s existence. Both companies have now released patches. They were joined by Mozilla, which released its own advisory on CVE-2023-4863 yesterday and updates for several versions of its Firefox browser and Thunderbird email client, and Microsoft.
Vulnerability Originates In Webp Reader. Users of the affected browsers should update to the most up-to-date version in order to ensure the zero-day vulnerability is patched on their machines. The problem isn’t with the browsers — the vulnerability originates in the WebP Codec. Many applications use the WebP codec and libwebp library to render WebP images.
In more detail, a heap buffer overflow in WebP allowed attackers to perform an out-of-bounds memory write. A heap buffer overflow allows attackers to insert malicious code by “overflowing” the amount of data in a program. Since this particular heap buffer overflow targets the codec (essentially a translator that lets a computer render WebP images), the attacker could create an image in which malicious code is embedded. From there, they could steal data or infect the computer with malware. The vulnerability was first detected by the Apple Security Engineering and Architecture team and The Citizen Lab at The University of Toronto on September 6.
Since many browsers, including Microsoft Edge, Brave, Opera, and Vivaldi are built on the Chromium platform, the same platform that Chrome is based on, this could affect their users as well. The same risk is also applicable for Firefox browser clones.
Such a widespread exploit in ubiquitously used software is dangerous, widening the attack surface for most organizations.
Patching will mitigate the risk, but users must act quickly as hackers will already be at work. Attackers will be working over the coming days and weeks to make the exploit more reliable meaning remote code execution will be more likely. Modern web browsers are exceptionally good at pushing out security updates rapidly and applying them as quickly as practicable, so users will shortly be protected.
The biggest risk is to organizations which don’t allow automatic updates and push out updates at their own release schedule.
Google, Mozilla, Brave, Microsoft and Tor have released security patches for this vulnerability. Individuals running those apps should update to the latest version. In the case of other applications, this is an ongoing vulnerability for which patches may not exist; NIST noted that the vulnerability has not yet received full analysis.
Google Chrome – Click the 3 dots in the top right corner for the menu and choose Help->About Google Chrome. Chrome will check and install updates automatically from this screen.
Microsoft Edge – Click the 3 dots in the top right corner for the menu and choose Help and feedback->About Microsoft Edge. Edge will check and install updates automatically from this screen.
Mozilla Firefox – Click the 3 lines in the top right corner for the menu and choose Help->About Firefox. Firefox will check and install updates automatically from this screen.
If you have any questions, please email us at support@sjtechies.com or call us at (856) 745-9990
Microsoft Office 2013 was a popular productivity suite that included several essential tools such as Word, Excel, PowerPoint, and Outlook. It was released in 2013 and was widely used by individuals, businesses, and organizations of all sizes. However, like all software products, Microsoft Office 2013 has reached its end of life, and users are now advised to upgrade to Microsoft 365, the cloud-based version of Microsoft Office.

End of life, or EOL, refers to the point in time when a software product is no longer supported by the manufacturer. In the case of Microsoft Office 2013, this means that Microsoft will no longer provide technical support, bug fixes, security updates, or new features for this product. This makes the software more vulnerable to cyberattacks, viruses, and malware. Continuing to use Microsoft Office 2013 after the end of life date could result in data loss, security breaches, and other serious problems.
If you’re using Office 2013, it’s probably a good time to upgrade your version of Microsoft Office.
The best way to protect yourself and your organization is to upgrade to a newer version of Office:
Microsoft 365 is an all-in-one cloud solution with a number of different licensing options to fit your organization’s needs. The best part about cloud-based applications is that you no longer have to worry about retirements, patches, and end of support. Cloud licenses are automatically updated with new features, new applications, and security updates. Many cloud subscriptions also include installed (or desktop) versions of the application, so you can have the same look and feel of the Office applications you are accustomed to using, but built with more robust features and benefits.
Office Home and Business 2021 is for families and small businesses who want classic Office apps and email. It includes Word, Excel, PowerPoint, and Outlook for Windows 11 and Windows 10. A one-time purchase installed on 1 PC or Mac for use at home or work.
If you have any questions, please email us at support@sjtechies.com or call us at (856) 745-9990.


The EU GDPR is a law designed to protect and empower residents of the EU by guiding business usage of personal data. In essence, it is reshaping the way corporations handle personal data by controlling its collection, use, and storage. It will replace the regulations and frameworks of the existing 20-year-old directive (95/46/EC).
The data subject: This is any individual that can be directly or indirectly identified or uniquely singled out in a group of individuals, from any stored data.
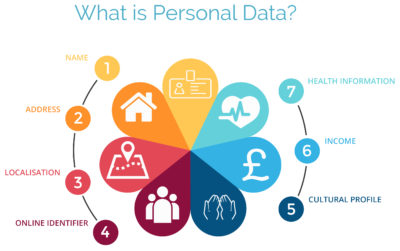
Personal data: This is any information relating to an individual, whether in reference to their private, professional, or public life. It includes things like names, photos, email addresses, location data, online identifiers, a person’s bank details, posts on social networking websites, medical information, work performance details, subscriptions, purchases, tax numbers, education or competencies, locations, usernames and passwords, hobbies, habits, lifestyles, or a person’s computer’s IP address.
The data controller: This is the person who, alone or jointly with others, determines the purposes for, and means of, processing personal data. A data controller is not responsible for the act of processing (this falls to the data processor); they can be defined as the entity that determines motivation, condition, and means of processing.
Generally, the role of the controller is derived from the organization’s functional relation with the individual. That is, a business is the controller for the customer data it processes in relation to its sales, and an employer is the controller for the employee data they process in connection with the employment relationship.

Data processors: This is the person who processes personal data on behalf of the controller. Typical processors are IT service providers (including hosting providers) and payroll administrators. The processor is required to process the personal data in accordance with the controller’s instructions and take adequate measures to protect the personal data. The GDPR does not allow data processors to use the personal data for other purposes beyond providing the services requested by the controller.
Processing refers to any operation or set of operations performed upon personal data, whether or not by automatic means—such as collection, recording, organization, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, blocking, erasure, or destruction. Processing must be fair and lawful, although transparency is significantly strengthened. The processor may not use the personal data for their own purposes.
Under the GDPR, data subjects can request the following:
We’re not done yet. There are four more important elements to consider with GDPR as you become ready.

For controllers, GDPR requires that breach notice must be provided, where feasible, within 72 hours of becoming aware of a breach; processors need to provide notice to controllers without undue delay. Any data breaches must be documented.
This requires the level and type of data being processed to be limited to the minimum amount of data necessary. This requires you to ensure that the purpose in which the data is agreed and the purpose in which the data was collected are materially similar. The processors should ensure that individuals’ privacy is considered at the outset of each new processing, product, service, or application, and only minimum amounts of data are processed for the specific purposes collected and processed.
The GDPR defines pseudonymization as “the processing of personal data in such a way that the data can no longer be attributed to a specific data subject without the use of additional information.” To pseudonymize data, the “additional information” must be “kept separately and subject to technical and organizational measures to ensure non-attribution to an identified or identifiable person.” In other words, it is a strategy designed to enhance protection and privacy for applicable identifying data.
Although similar, anonymization and pseudonymization are two distinct techniques that permit data controllers and processors to use de-identified data. The difference between the two techniques rests on whether the data can be re-identified.
This requires the processing of personal data to be fair and lawful. Generally, only the level and type of data collected should be limited to the minimum amount of data necessary (see data minimization above). There are a number of methods in which the data may be processed, including: express consent (which may be withdrawn at any time), legitimate interest basis (the subject of which legitimacy may be challenged by the data subject), honoring obligations under the agreement with the data subject, or any other legal basis that may apply.
We know this information can be overwhelming, but taking the proper steps now will save you headaches later. SolarWinds provides products that can help you with getting ready. Our Risk Intelligence software is one of them, providing you with hard data on:
Search your ‘data at rest’ for risk areas and start the data mapping you need to get ready for GDPR.
National Cyber Security Awareness Month encourages vigilance and protection by sharing tips and best practices in regard to how to stay safe.
Small businesses are a large target for criminals because they have limited resources dedicated to information system security. Cyber criminals look for access to sensitive data.
The Federal Communications Commission offers a Cyber Planner for small businesses. The planner guide allows specific sections to be added to your guide, including Privacy and Data Security, Scams/Fraud, Network Security, Website Security, Email, Mobile Devices, Employees, Facility Security, Operational Security, Payment Cards, Incident Response/Reporting and Policy Development/Management.
Generate a personalized Small Biz Cyber Planner Guide.
Create rules and guidelines for protecting information. Educate employees on how to post online in a way that does not share intellectual property. Clearly explain the penalties for violating security policies.
Deploy and update protection software, such a antivirus and antispyware software, on each computer within your network. Create a regularly scheduled full computer scan.
Cyber criminals often use small businesses that are less-protected to get to larger businesses. Being a victim of a cyber-attack can have a huge impact on any business including financial issues, loss of possible business partner(s) and many more issues.
Installing software updates from vendors can protect your network for unwanted viruses and malware. Vendors frequently release patches/updates for their software to improve performance and fine-tune software security. (Example: Adobe Reader, Adobe Flash and Java updates are critical for protection.)
Create a backup plan for all data including documents, databases, files, HR records and accounting files. A regularly scheduled backup can be a full, differential or incremental.
Protecting physical property is a very important role in protecting intellectual data. Create a physical security plan to prevent unauthorized access to business computers and components.
Securing your Wi-Fi network consists of a few configurations. Configure a device administrator password for your wireless access point (WAP) or router, require a password for Wi-Fi access and do not allow the WAP or router to broadcast the Service Set Identifier (SSID), also known, as network name.

Microsoft is previewing Stream, a new service for publishing and managing business videos. One day it will be the default video publishing system for Office 365.
On July 18, 2016, Microsoft announced that a preview version of a new service called Microsoft Stream was available. Like most of you, I passed over the news with an indifferent “whatever” attitude. But later I realized that the news was actually more important than I had first thought.
Microsoft Stream fulfills a niche by providing a secure place to share videos created within, and for, businesses. By using a cloud-based service like this, businesses can reap the benefits of video communication without the threat of anonymous forum trolls trashing the brand or harassing employees.
While it is still a preview version, Microsoft Stream seems mostly ready for prime time. All you have to do is set up an account with a valid business email—One can use a personal domain email—and then log in. To test how easy Stream is to work with, you can make a 10-second video with a smartphone. Upload your video to Google Drive and then drag and drop it on the Stream portal website.
The web service processes the video while you give it a title and a brief description. Stream then asks if you are ready to publish and when you say yes, it publishes the video after a few seconds of grinding. It takes all of two minutes from start to finish and requires nothing more technical than knowing how to drag and drop a file.
Gone are the days of worrying about file format, aspect ratio, preferred playback applications, and all the other minutia we had to go through in years past to get a video published. You just take the video and then publish the video.
The key features of Microsoft Stream have to do with managing videos after they are published. Videos can be classified and placed into specific channels. Those channels can have their access restricted to certain individuals or certain groups, like a specific department, for instance. Access is controlled via the Azure Active Directory system.
According to the blog post, Microsoft plans to integrate Stream into the existing Office 365 Video system. Once the integration is complete, Microsoft Stream will be the default system for publishing video in an Office 365 environment.
There are plans in the works to add intelligent search to Stream by taking advantage of tools like audio transcription and face recognition. Developers are also working on ways to integrate Stream with other tools, like PowerApps, Microsoft Flow, and SharePoint.
We are aware of Microsoft Bookings and how that application attempts to cut out other third-party developers by integrating appointment scheduling for small businesses with the standard Office 365 subscription. By offering Stream, a secure video publishing and management service, Microsoft is attempting to execute the same strategy for video publishing.
Microsoft Stream gives businesses a secure system for publishing videos. Through Stream, businesses control access and manage who can see what and when they can see it. And because it is all handled internally, problems with anonymous forum trolls are likely to be reduced.
It seems that Microsoft’s grand strategy is to become the only software company a business needs—ever. The glaring application that Office 365 is missing now is a double-entry accounting system that includes payroll, accounts receivable, accounts payable, and the general ledger. Should we be looking for an announcement regarding those applications soon, Microsoft?
Get answers from Microsofts Cloud Solutions Partner!
Call us at: 856-745-9990 or visit: https://southjerseytechies.net/
South Jersey Techies, LL C is a full Managed Web and Technology Services Company providing IT Services, Website Design Services, Server Support, Network Consulting, Internet Phones, Cloud Solutions Provider and much more. Contact for More Information.
To read this article in its entirety click here.

Tracking and reporting activity in Office 365 using the built-in admin tools is about to get much better. Here’s what the revamped admin center has to offer.
Gathering usage information about Microsoft Office 365 in an enterprise is limited by the available admin tools. To make matters worse, as Microsoft adds new applications to Office 365, the ability to track if, and how, users were consuming the new features has been even more difficult. But with the rollout of the new Office 365 admin center in March 2016, those limitations are quickly disappearing.
At first glance, you may think the main activity for any Office 365 admin is adding and subtracting employees from the active roster. But a good admin should be doing much more.
As the number of applications in Office 365 has grown substantially in recent years, the need to track all Office 365 activity has also grown. This need to track activity is especially important in larger enterprises where mishandled resources can raise overall costs significantly.
For example, knowing how many employees actually use Yammer on a weekly basis, and when, could help admins predict when resources will be taxed the most. Or tracking how users are actually using collaboration tools like Skype and Delve may lead an admin to conclude that more training on those applications is needed because the apps are underutilized. These are the sort of questions the new Office 365 admin center is looking to answer.
By simplifying the interface and creating ready-to-use dashboards, Microsoft is trying to streamline the reporting process. Tracking email activity and other peak usage data is just a few clicks away. And as the new Office 365 admin center is rolled out, there will also be tools admins can use to create custom reports.
Speaking from personal experience, the new admin dashboard interface is a welcome improvement. Navigation in the new admin center closely matches the familiar navigation system of other Office 365 apps. The previous admin center, with its heavy use of linked text, looked almost tacked on as an afterthought.
The new Office 365 admin center is rolling out in the United States right now and will be the default reporting experience very soon. The new center will roll out to other parts of the world in April 2016.
If you’re not ready for the change, you can roll back to the old admin system during this introductory phase. On the other hand, if you’re anxious for a change, you can click the Get A Sneak Peek link at the top of the old Office 365 admin center to force the installation of the new system.
For most users, administering Office 365 is someone else’s responsibility, but that does not diminish its importance to an enterprise.
A good admin should be able to track what activity is taking place within Office 365 and, more important, what activity is not taking place. Knowing who uses what applications for how long, and when, is essential information. Armed with that knowledge, administrators can determine how to better allocate resources and where new training for users may be required.
With the rollout of the new Office 365 admin center, Microsoft is using feedback received from its customers to create tools and dashboards that it hopes will make the tracking of vital activity data in Office 365 an easily achieved reality.
Get answers from Microsofts Cloud Solutions Partner!
Call us at: 856-745-9990 or visit: https://southjerseytechies.net/
South Jersey Techies, LL C is a full Managed Web and Technology Services Company providing IT Services, Website Design Services, Server Support, Network Consulting, Internet Phones, Cloud Solutions Provider and much more. Contact for More Information.
To read this article in its entirety click here.

